AWS Authentication & Permission (IAM)
AWS Identity and Access Management (IAM) Cheatsheet
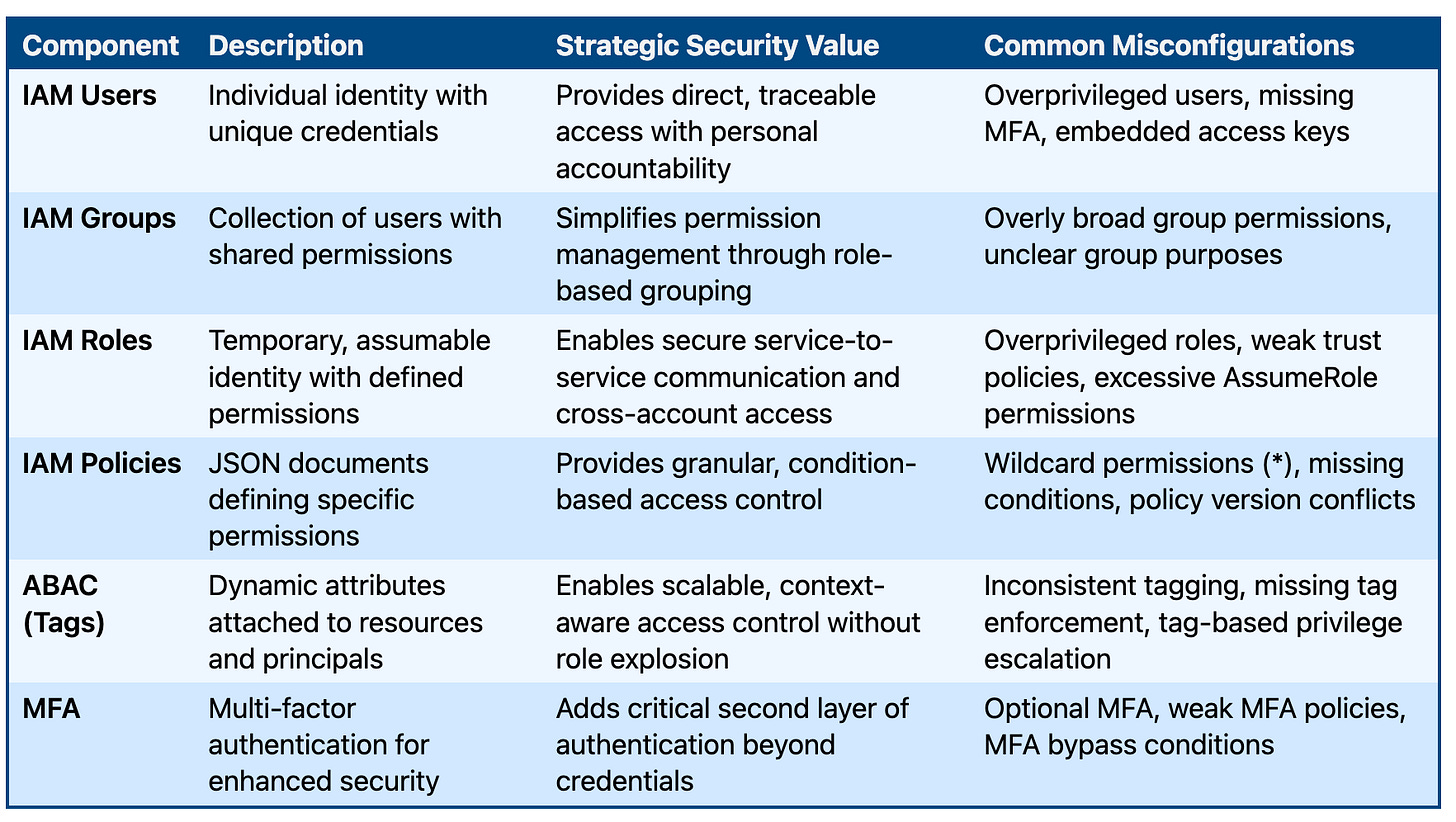
Picture
AWS Identity and Access Management (IAM) as the grand library of Alexandria reimagined for the digital age—a vast repository where every scroll, tome, and secret manuscript requires precise authentication and granular permissions. In this intricate realm of cloud security, IAM serves as both the master librarian and the architect of knowledge access, determining not just who can enter the sacred halls, but which specific books they can read, which secrets they can unlock, and which forbidden knowledge remains forever beyond their reach.
This comprehensive guide presents an epic intellectual battle between two formidable minds: "Cipher", a sophisticated digital infiltrator who exploits IAM weaknesses with the cunning of a master thief navigating ancient security systems, and "Guardian", an elite cloud security architect who wields advanced IAM strategies like a chess grandmaster orchestrating an intricate game of identity and access. Through their strategic warfare, we'll explore real-world attack vectors, defensive countermeasures, and the ever-evolving landscape of cloud identity security.
In today's cloud-first ecosystem, where microservices dance in complex choreography across hundreds of integrated platforms, traditional perimeter-based security crumbles like ancient castle walls against modern siege engines. AWS IAM emerges as the new paradigm—a sophisticated framework that transcends simple authentication to orchestrate a symphony of fine-grained permissions through policies, roles, and dynamic attribute-based access controls that adapt seamlessly to cloud-native architectures.
Learning Objectives
By the end of this comprehensive IAM security deep dive, you will:
Master AWS Identity Architecture: Gain deep understanding of IAM components including users, groups, roles, policies, and advanced authentication mechanisms like MFA and federation.
Decode Advanced IAM Attack Vectors: Learn sophisticated methods attackers use to exploit IAM misconfigurations, including privilege escalation, credential theft, policy manipulation, and ABAC bypass techniques.
Architect Robust IAM Defense Systems: Gain expertise in implementing layered IAM security using ABAC, least-privilege policies, MFA enforcement, continuous monitoring, and proactive threat detection.
Navigate Real-World IAM Scenarios: Analyze detailed attack and defense scenarios, applying learned concepts in multi-tenant environments, enterprise contexts, and dynamic cloud-native applications.
Deploy Advanced IAM Security Tools: Master AWS Config for IAM compliance, Access Analyzer for policy validation, CloudTrail for identity forensics, and GuardDuty for behavioral anomaly detection.
Implement Attribute-Based Access Control (ABAC): Design and deploy dynamic, tag-based access control systems that scale efficiently with modern cloud architectures while maintaining security granularity.
The AWS IAM Ecosystem: Identity Architecture in the Cloud Age
Before diving into the tactical cyber warfare between Cipher and Guardian, let's explore the IAM landscape that makes cloud identity security both critically important and inherently complex.
Core IAM Concepts: The Building Blocks of Cloud Identity
Principal: The entity making a request - users, roles, federated identities, or AWS services
Authentication: Verifying the identity of the principal (proving "who you are")
Authorization: Determining what the authenticated principal can do (defining "what you can access")
Policy: JSON documents that formally define permissions and can be attached to identities or resources
Attribute-Based Access Control (ABAC): Dynamic permission system using tags and contextual conditions for scalable access management