AWS Proactive Defence: The Art of War in Cloud Security
The art of AWS proactive defence lies in understanding these attack patterns and positioning your defenses not where you think attacks might occur, but where they *must* occur to be successful.
Picture AWS as a vast digital metropolis—millions of services running 24/7, data flowing like rivers through interconnected highways, and somewhere in this complexity, adversaries are constantly probing for weaknesses. Proactive defence isn't about reacting to threats; it's about creating an environment where threats reveal themselves the moment they attempt to establish presence.
Modern cloud attacks follow predictable patterns, much like military campaigns. They begin with reconnaissance, escalate through initial access, expand via lateral movement, establish persistence, and culminate in impact or exfiltration. Each phase presents opportunities for defenders to disrupt the attack chain, but only if the right defensive measures are in place.
The art of AWS proactive defence lies in understanding these attack patterns and positioning your defenses not where you think attacks might occur, but where they must occur to be successful.
Offensive TTPs: Understanding the Enemy
Initial Access: The Digital Front Door
Attackers seeking initial access to AWS environments typically exploit one of several common vectors:
Credential Harvesting and Abuse
The most common entry point remains compromised credentials. These often surface through:
# Common reconnaissance commands attackers use
aws sts get-caller-identity
aws iam list-roles
aws ec2 describe-instances
aws s3 ls
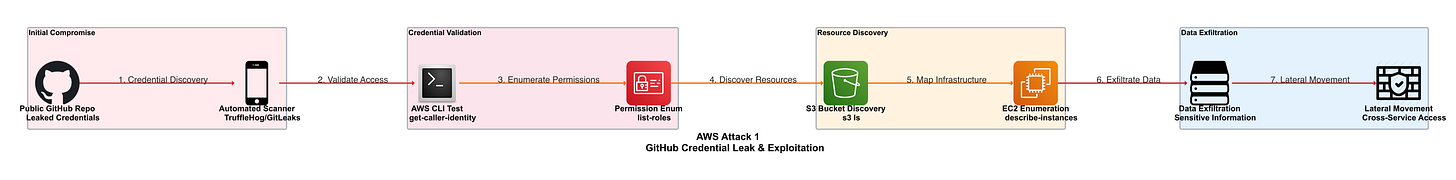
GitHub Credential Leak Attack Flow:
The diagram above illustrates how attackers discover exposed AWS credentials in public repositories and exploit them systematically. The attack progresses from automated credential scanning through validation, enumeration, resource discovery, and ultimately data exfiltration with lateral movement capabilities.
Attack Flow Diagram:
Console Login Without MFA
A classic attack vector that continues to plague organizations:
# Stratus Red Team simulation
stratus warmup aws.initial-access.console-login-without-mfa
stratus detonate aws.initial-access.console-login-without-mfa
Credential Access: The Keys to the Kingdom
Once inside, attackers focus on credential harvesting to expand their access:
EC2 Instance Metadata Service (IMDS) Exploitation
The IMDS remains a critical attack vector, especially with IMDSv1:
# SSRF payload targeting IMDS
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/[role-name]
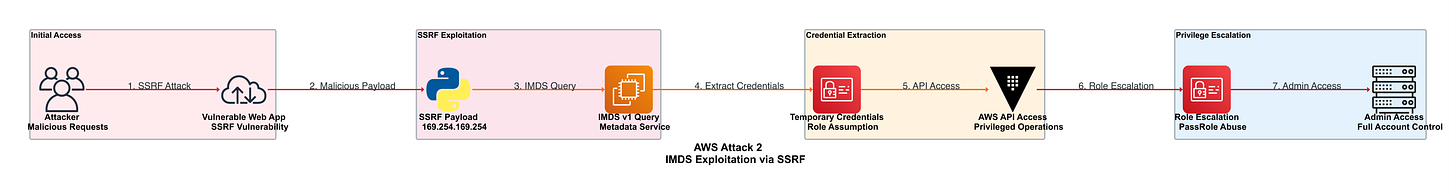
IMDS SSRF Attack Flow:
This visualization demonstrates how Server-Side Request Forgery (SSRF) vulnerabilities can be exploited to access the EC2 Instance Metadata Service (IMDS) for credential extraction. The attack flow shows progression from SSRF vulnerability exploitation through metadata service access, credential extraction, and privilege escalation to full account control.
IMDS Attack Chain:
Secrets Manager Mass Extraction
Attackers often attempt bulk extraction of secrets:
# Stratus simulation for secrets extraction
stratus warmup aws.credential-access.secretsmanager-retrieve-secrets-batch
stratus detonate aws.credential-access.secretsmanager-retrieve-secrets-batch
Privilege Escalation: Climbing the Ladder
PassRole Exploitation
The iam:PassRole permission is frequently misconfigured, allowing privilege escalation:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "iam:PassRole",
"Resource": "*"
}
]
}
PassRole Attack Sequence:
Persistence: Maintaining the Foothold
IAM Backdoors
Attackers establish persistence through various IAM manipulations:
# Creating backdoor user
aws iam create-user --user-name backup-service-user
aws iam create-access-key --user-name backup-service-user
aws iam attach-user-policy --user-name backup-service-user --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
Lambda Function Backdoors
Lambda functions provide excellent persistence mechanisms:
import boto3
import base64
def lambda_handler(event, context):
# Backdoor functionality
if event.get('backdoor') == 'execute':
command = base64.b64decode(event['cmd']).decode()
# Execute system commands
return {"status": "executed", "output": "command_output"}
Defense Evasion: Hiding in Plain Sight
CloudTrail Disruption
Attackers often target logging mechanisms:
# Stratus simulation for CloudTrail evasion
stratus warmup aws.defense-evasion.cloudtrail-delete
stratus detonate aws.defense-evasion.cloudtrail-delete
CloudTrail Evasion Chain: