HTTP Request Smuggling: The Silent Protocol Desync Attack
When proxies speak different dialects of HTTP, attackers find the gaps between words.
“When proxies speak different dialects of HTTP, attackers find the gaps between words.”
The Hidden War at Protocol Boundaries
Picture a high-security vault with two guards—one at the front gate, one inside. Both speak English, but interpret sentences differently. An attacker crafts a message that means “I’m just a visitor” to the first guard, but secretly encodes “Give me the master key” to the second. This is HTTP Request Smuggling—a devastating attack exploiting protocol desynchronization between frontend proxies and backend servers.
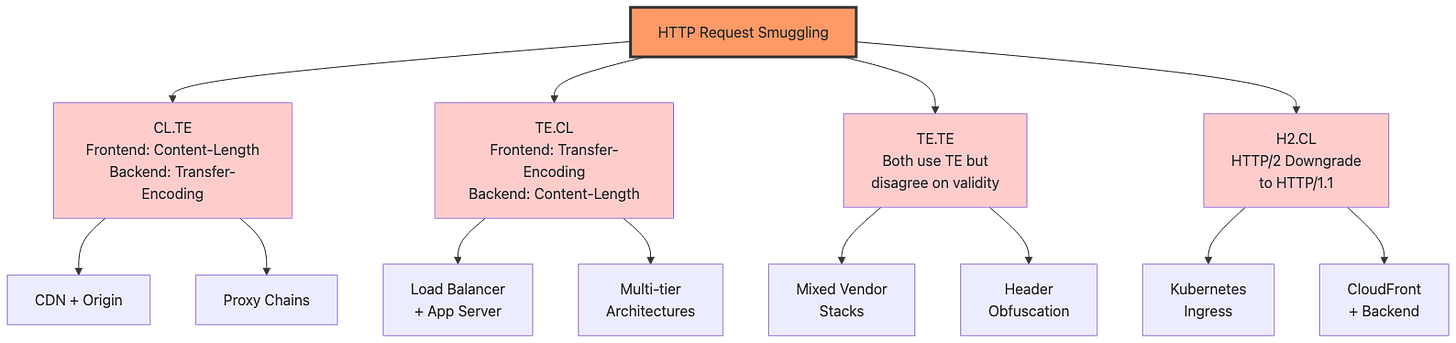
Attack Variants at a Glance
HTTP/1.1: The Fundamental Protocol Flaw
Why HTTP/1.1 Must Be Disabled - PortSwigger’s Latest Research (2025)
Critical Finding: At Black Hat USA and DEF CON 33 (2025), James Kettle, Director of Research at PortSwigger, issued an industry-wide call: “HTTP/1.1 must die.” After six years of continuous research across four waves of attack discovery, PortSwigger has concluded that HTTP Request Smuggling is not a configuration bug—it’s an inherent protocol flaw baked into HTTP/1.1’s architecture.
The Protocol Design Flaw
HTTP/1.1 (RFC 7230) was designed with ambiguous message boundary definitions. The specification provides multiple, sometimes conflicting mechanisms to delimit request/response bodies:
Content-Length: Explicit byte count
Transfer-Encoding: chunked: Size-prefixed chunks with terminator
Content-Length + Transfer-Encoding: Undefined precedence in legacy systems
Keep-Alive semantics: Connection reuse without protocol safeguards
This intentional flexibility created a parsing lottery where different implementations interpret the same bytes differently.
┌─────────────────────────────────────────────────────────────┐
│ HTTP/1.1 AMBIGUITY MATRIX │
├─────────────────────────────────────────────────────────────┤
│ Header Combination │ RFC 7230 Guidance │
├──────────────────────────────────────────────────────────────┤
│ CL + TE │ "Remove CL" (ignored by many) │
│ Multiple CL values │ "Must be identical" (unsafe) │
│ Multiple TE values │ "Invalid" (lenient parsers OK) │
│ TE with obs-fold │ Backward compat trap │
│ 0-length body │ Valid but deferred parsing │
└──────────────────────────────────────────────────────────────┘
Why HTTP/1.1 Cannot Be Fixed
Attempt #1 - RFC 7230 Clarification: Added guidance in HTTP/1.1 update (2014)
Result: Legacy proxies/servers already deployed; no enforcement mechanism
Attempt #2 - Server-Side Strictness: Tomcat, Nginx added “strict mode” flags
Result: Frontend proxies still lenient; attacker targets desync between layers
Attempt #3 - WAF Detection Rules: Block CL+TE combinations
Result: Attackers use obfuscation (spaces, line folding, capitalization); evasion arms race
Attempt #4 - Per-Request Connection Reuse Restrictions: Kill Keep-Alive
Result: Incompatible with modern CDN architectures (connection pooling); performance kills
Fundamental Problem: The vulnerability exists because HTTP/1.1 allows multiple valid interpretations of the exact same bytes. No configuration change can fix this.
The Four Attack Waves of HTTP/1.1
PortSwigger has identified these successive attack evolution patterns:
WAVE 1 (2018): CL.TE + TE.CL + TE.TE
└─ Basic parser desync; affects traditional architectures
WAVE 2 (2020): Request Smuggling Cache Poisoning
└─ Targets CDN caching layers; persistent compromise
WAVE 3 (2022): Browser Cache Poisoning via HTTP/2 Downgrade
└─ H2.CL attacks; affects all modern browsers via session fixation
WAVE 4 (2025): Multi-Tenant Isolation Breaches
└─ Kubernetes + Serverless; tenant data cross-contamination
Exploits: Protocol translation layers, container checkpoint confusion
Comparison: HTTP/1.1 vs HTTP/2 vs HTTP/3
Disabling HTTP/1.1: Implementation Guide
Step 1: Web Server Configuration
Nginx: Disable HTTP/1.1 Entirely
server {
# Disable HTTP/1.0 and HTTP/1.1 - Accept only HTTP/2+
# Redirect HTTP/1.1 clients to HTTPS with HTTP/2
listen 443 ssl http2 only;
listen [::]:443 ssl http2 only;
# Explicitly reject HTTP/1.1 upgrade attempts
if ($server_protocol = "HTTP/1.1") {
return 426 "Upgrade Required";
}
# Send Upgrade header for HTTP/1.1 clients
add_header Upgrade h2 always;
add_header Connection upgrade always;
}
Apache 2.4: Disable HTTP/1.1 Protocol Module
# In /etc/apache2/mods-available/http2.conf or httpd.conf
Protocols h2 h2c
Tomcat 9/10: Force HTTP/2 on HTTPS Connectors
<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol"
scheme="https" secure="true"
sslProtocol="TLSv1.2,TLSv1.3"
allowCipherSuiteName="true"
ciphers="HIGH:!aNULL:!MD5"
compressionMinSize="0">
<!-- Disable HTTP/1.1 Keep-Alive entirely -->
<UpgradeProtocol className="org.apache.coyote.http2.Http2Protocol" />
</Connector>
Step 2: Load Balancer Configuration
AWS ALB: Enforce HTTP/2