Insecure by Design: The Vibe Coding Misunderstanding Crisis
Vibe coding has transformed software development by democratizing programming through AI-assisted tools like GitHub Copilot, Cursor, Windsurf, and Claude Code.
Vibe coding has transformed software development by democratizing programming through AI-assisted tools like GitHub Copilot, Cursor, Windsurf, and Claude Code. However, this “forget that the code even exists” mentality has created a new category of systematically vulnerable applications.
This playbook examines multi-technology attack scenarios where vibe coding misunderstandings create exploitable vulnerabilities across .NET/ASP.NET Core, C/C++, Java/Spring, JavaScript, and Python ecosystems. We provide defensive strategies, AI assistant rules files, and detection patterns to transform vibe coding from a security liability into a secure-by-default development accelerator.
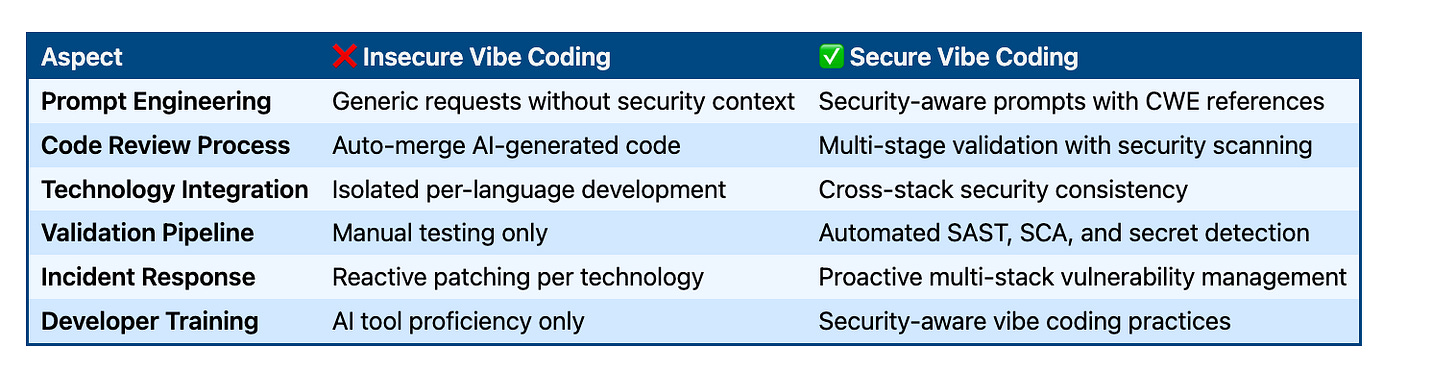
Architecture Analysis: Insecure vs Secure Vibe Coding Patterns
Multi-Technology Attack Scenarios: Exploiting Vibe Coding Vulnerabilities
1. .NET/ASP.NET Core: Authorization Bypass Through Missing Attributes
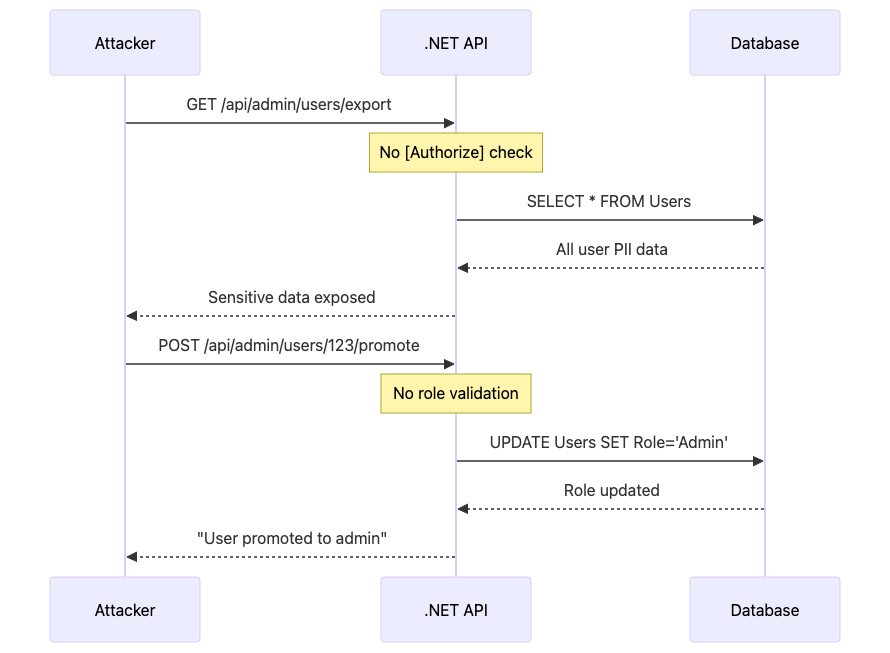
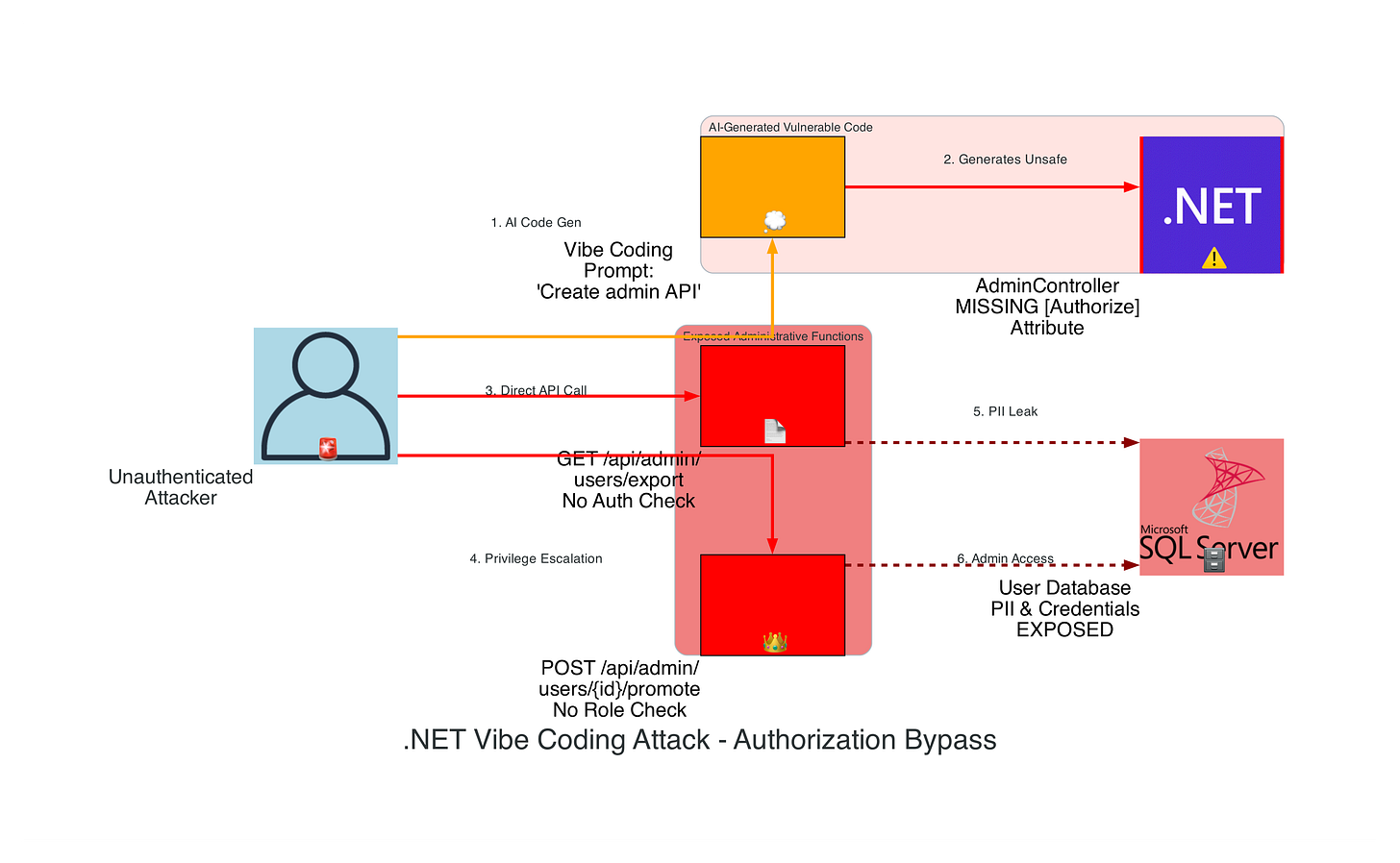
Attack Scenario: Vibe-coded controllers missing [Authorize] attributes expose administrative functions to unauthenticated users.
Offensive Implementation
// AI-generated vulnerable controller - missing authorization
[ApiController]
[Route(”api/[controller]”)]
public class AdminController : ControllerBase
{
private readonly IUserService _userService;
public AdminController(IUserService userService)
{
_userService = userService;
}
// VULNERABILITY: No [Authorize] attribute
[HttpGet(”users/export”)]
public async Task<IActionResult> ExportAllUsers()
{
var users = await _userService.GetAllUsersWithSensitiveDataAsync();
return Ok(users); // Exposes PII to anyone
}
// VULNERABILITY: No role-based authorization
[HttpPost(”users/{id}/promote”)]
public async Task<IActionResult> PromoteToAdmin(int id)
{
await _userService.GrantAdminRoleAsync(id);
return Ok(”User promoted to admin”);
}
}
Attack Sequence Diagram
Visual Attack Flow:
Defensive Implementation
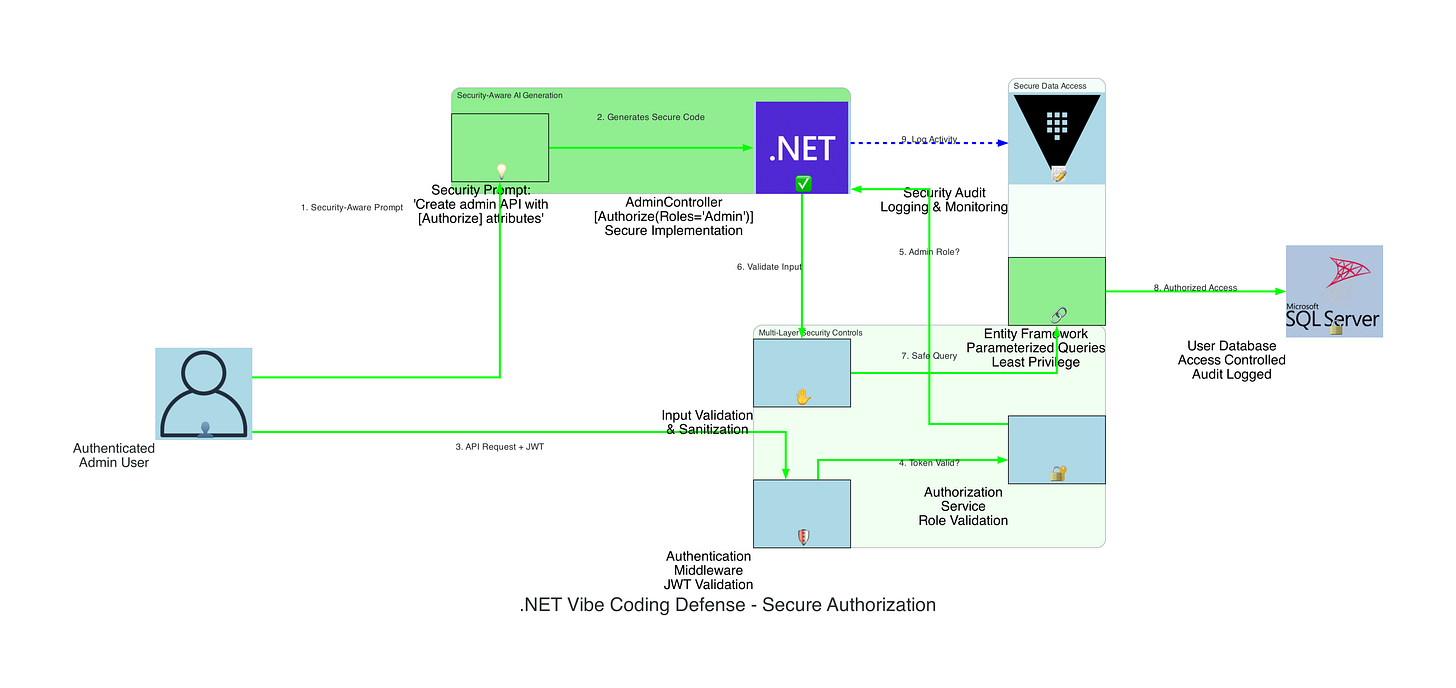
// Security-aware AI-generated controller
[ApiController]
[Route(”api/[controller]”)]
[Authorize(Roles = “Administrator”)] // Global authorization requirement
public class AdminController : ControllerBase
{
private readonly IUserService _userService;
private readonly IAuthorizationService _authorizationService;
public AdminController(IUserService userService, IAuthorizationService authorizationService)
{
_userService = userService;
_authorizationService = authorizationService;
}
[HttpGet(”users/export”)]
public async Task<IActionResult> ExportAllUsers()
{
// Additional authorization check for sensitive data
var authResult = await _authorizationService.AuthorizeAsync(User, “DataExportPolicy”);
if (!authResult.Succeeded)
{
return Forbid(”Insufficient privileges for data export”);
}
var users = await _userService.GetUsersForExportAsync(); // Returns sanitized data
return Ok(users);
}
[HttpPost(”users/{id}/promote”)]
public async Task<IActionResult> PromoteToAdmin(int id)
{
// Verify super admin role for privilege escalation
if (!User.IsInRole(”SuperAdministrator”))
{
return Forbid(”Only super administrators can promote users”);
}
await _userService.GrantAdminRoleAsync(id);
return Ok(”User promoted with proper authorization”);
}
}
Visual Defense Architecture:
Semgrep Detection Rule
rules:
- id: missing-authorize-attribute
pattern: |
[ApiController]
...
public class $CLASS : ControllerBase
{
...
[Http$METHOD(”...”)]
public ... $ACTION(...)
{
...
}
}
pattern-not: |
[Authorize]
...
[Http$METHOD(”...”)]
public ... $ACTION(...)
message: “Controller action missing [Authorize] attribute - potential unauthorized access”
severity: ERROR
languages: [csharp]
Claude Prompt for Secure .NET Generation
You are a security-focused .NET/ASP.NET Core developer. Generate code that:
- Always applies [Authorize] attributes to controllers unless explicitly documented with [AllowAnonymous]
- Uses IAuthorizationService for complex authorization logic
- Implements proper input validation using Data Annotations or FluentValidation
- Stores secrets in Azure Key Vault or user secrets during development
- Uses Entity Framework with parameterized queries, never string concatenation
- Includes comprehensive error handling without information disclosure
- Applies the principle of least privilege to all data access operations
Focus on OWASP ASVS Level 2 compliance for authentication and authorization controls.