Secret Alternatives for DevSecOps Engineers
some techniques to reduce use secret for devops environments and cloud native apps
Picture this: It’s 3:17 AM on a Saturday, and a cryptocurrency trading platform just discovered their entire AWS infrastructure is mining Bitcoin for someone else. The attack vector? A hardcoded AWS secret key committed to GitHub 18 months ago that nobody remembered existed. Within 72 hours, the attackers spun up 847 EC2 instances across 12 regions, generating $2.3 million in compute charges. Now imagine instead, they had implemented workload identity federation where credentials auto-rotate every hour and never touch disk or memory in plaintext. Same infrastructure, zero hardcoded secrets, attack impossible.
Secrets management is broken. Every security engineer knows this. Yet organizations continue treating API keys, database passwords, and cloud credentials like configuration files instead of the toxic assets they actually are. The modern approach? Stop using secrets altogether. Workload Identity Federation, SPIFFE/SPIRE, and OIDC-based authentication changed the game by eliminating the “bottom turtle problem” where accessing one secret requires another secret, creating infinite recursion.
Understanding the Secret Problem: The Foundation
What Are Secrets in Cloud-Native Environments?
Secrets are sensitive data required for authentication spanning database credentials used by applications to connect to PostgreSQL or MongoDB, cloud provider access keys enabling AWS S3 bucket access or Azure Blob operations, API tokens for third-party service integrations like Stripe or Twilio payment gateways, TLS certificates securing service-to-service communication in microservices architectures, and SSH private keys granting server access for deployment automation.
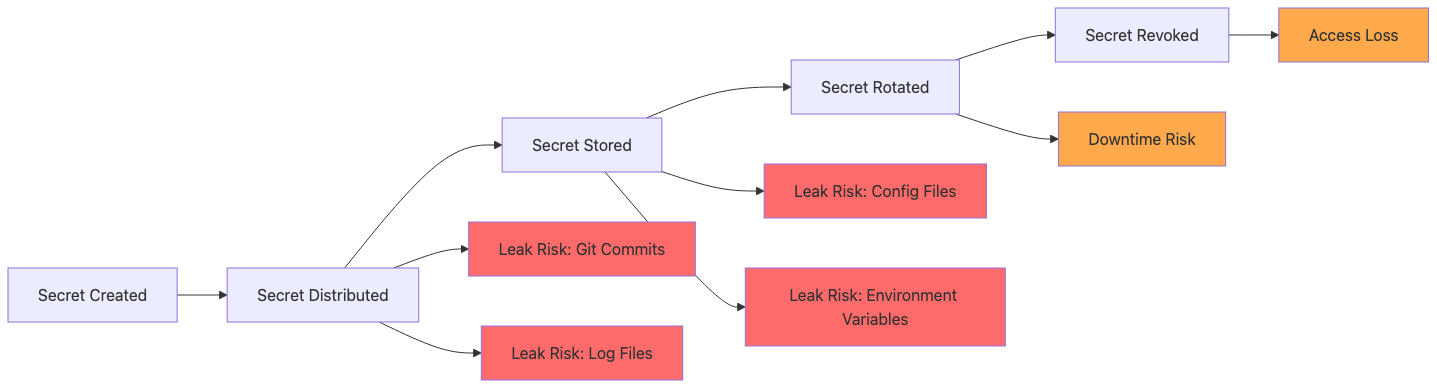
The Lifecycle Nightmare
Traditional secrets management creates operational hell:
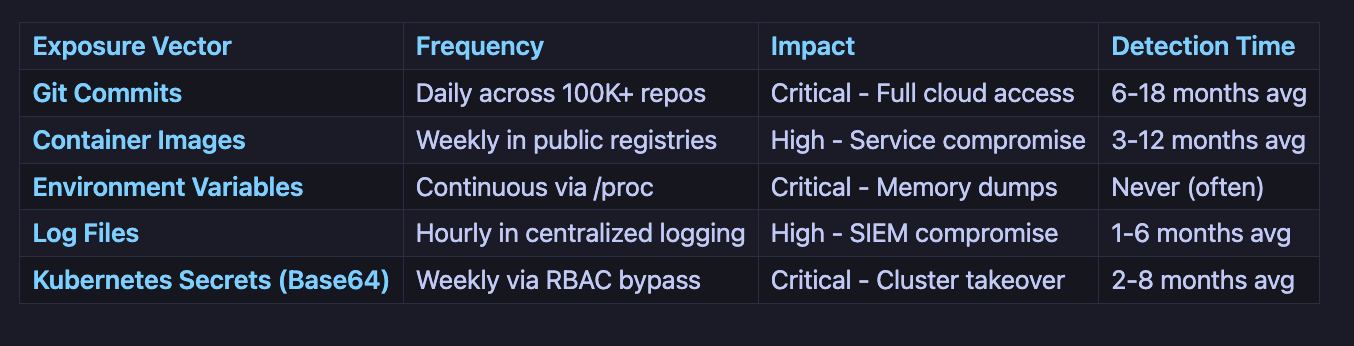
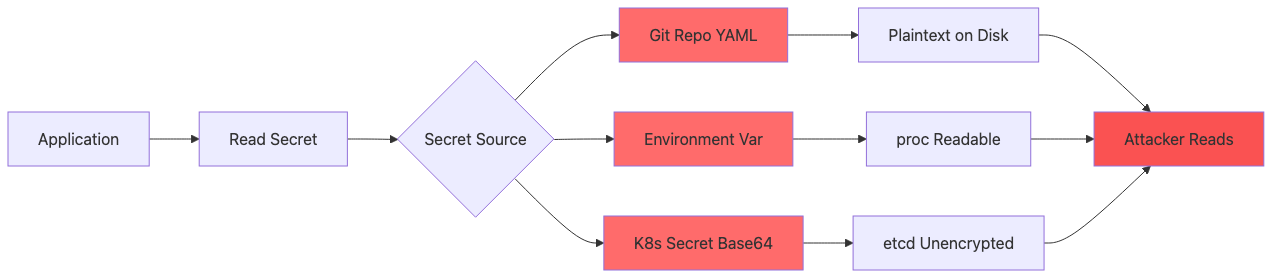
Types of Secret Exposure
The Architecture Landscape
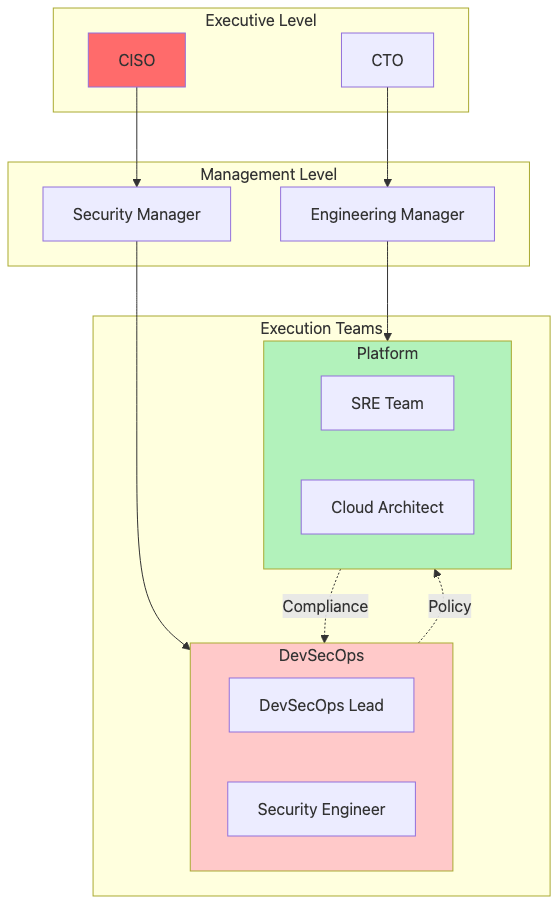
Organizational Structure for Secret Management
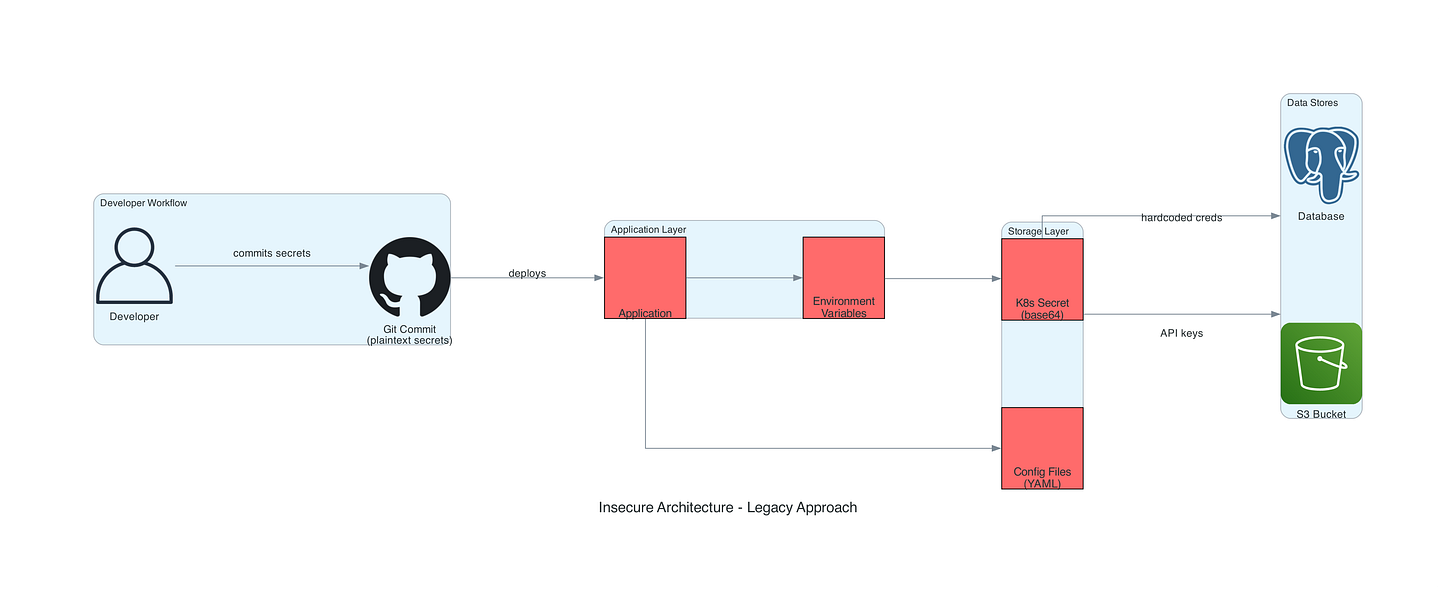
Insecure Architecture: The Legacy Approach
Organizations store database passwords in plaintext YAML files committed to Git repositories, hardcode AWS access keys directly in application source code without rotation mechanisms, pass secrets through environment variables readable via container runtime inspection, use Kubernetes Secrets encoded only in Base64 providing zero encryption, maintain shared service account credentials across teams without individual attribution, lack centralized secret rotation causing manual updates across hundreds of microservices, and embed TLS private keys in Docker images pushed to public registries.
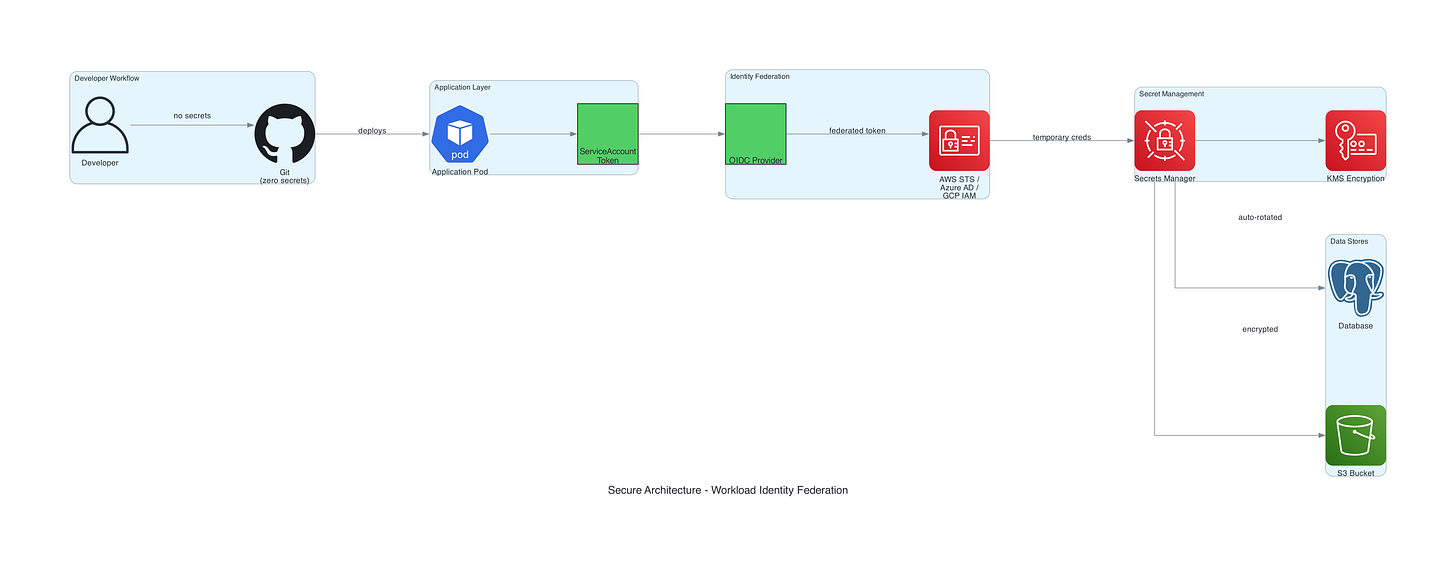
Secure Architecture: Workload Identity Federation
A secretless architecture eliminates static credentials entirely:
Security Controls:
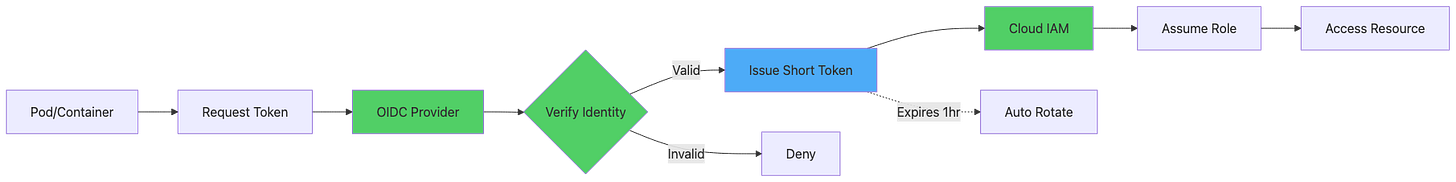
The modern approach demands cryptographic workload identity verified through OIDC token exchange, short-lived credentials with 15-60 minute TTL preventing long-term compromise, automatic credential rotation without application code changes, fine-grained IAM policies scoped to specific workloads not shared service accounts, complete audit trails in cloud provider logs tracking every authentication attempt, zero secrets stored on disk or in environment variables, and mTLS-based service mesh authentication for inter-service communication.
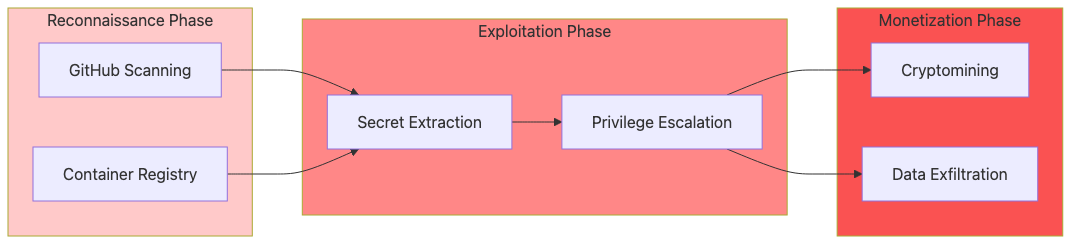
Attack Vectors: The Offensive Playbook
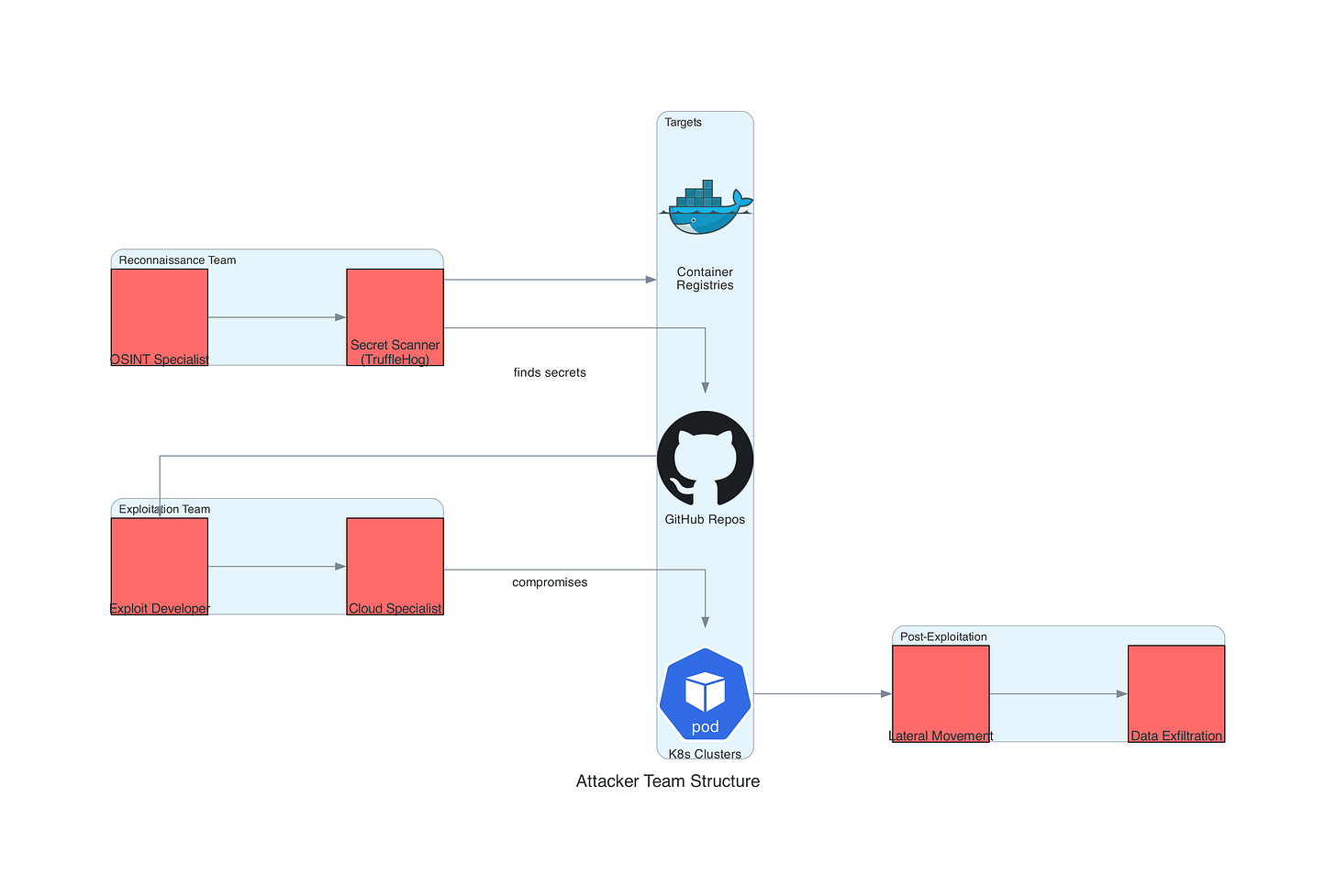
Attacker Team Structure and Methodology
Attack Technique #1: GitHub Secret Mining and AWS Credential Abuse
MITRE ATT&CK Mapping: T1552.001 (Credentials In Files), T1078.004 (Cloud Accounts)