Secure by Design Access Control: Middleware Playbook (2025)
In this playbook we harden the middleware tier that arbitrates access across APIs and services.
1. Prologue – The Invisible Border Guard
In every modern platform there is a silent parliament deciding who may act, view, mutate, approve, escalate, or exfiltrate. Breaches rarely begin with zero‑day RCE theatrics; they begin with an over‑permissive role, a stale token, a forgotten policy exclusion, a trust assumption (“it’s internal traffic”), or a missing re‑auth on a high‑risk path. Access control is where intent meets enforcement. Done carelessly, it converts architecture into an honor system. Done Secure‑by‑Design, it becomes a living adaptive contract.
In this playbook we harden the middleware tier that arbitrates access across APIs and services.
NO “magic trust zones”. Every request is interrogated. Every decision is explainable. Every privilege is least, time‑boxed, and contextual.
2. RBAC Middleware – From Static Lists to Policy Fabric
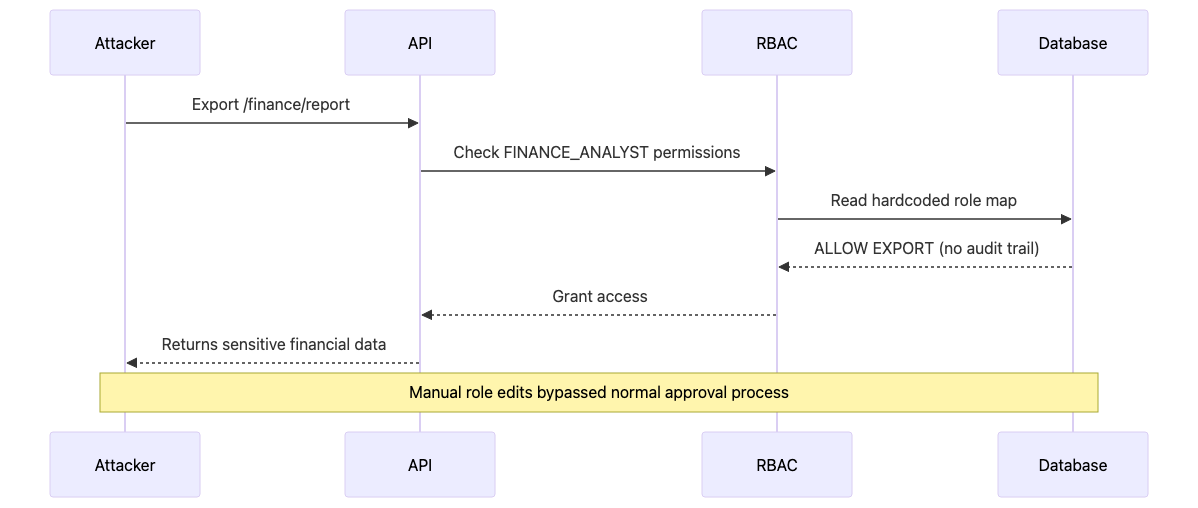
Story: "The Promotion That Wasn't Logged" - An internal finance API granted FINANCE_ANALYST read access. A hurried ops script manually edited a role → permissions map to unblock a report. Weeks later a contractor still had export capability; audit logs lacked the decision trace. Exfiltration disguised as normal export volume passed undetected.
Insecure Architecture:
Hardcoded Role Maps:
Map<Role, Set<Permission>>stored directly in application code, making changes require full deployments and bypassing change management processesMissing Context Evaluation: No consideration of risk factors like time-of-day, IP reputation, or device posture during authorization decisions
Audit Trail Gaps: Incomplete logging with partial events stored in plaintext, lacking integrity verification and tamper detection
Configuration Drift: No automated detection when role mappings change outside of approved processes, leading to shadow privileges
Secure Architecture:
External Policy Engine: Centralized OPA/Cedar policy decisions with API-driven evaluation, separating policy logic from application code
Rich Context Integration: Real-time risk scoring incorporating device posture, geo-location, and behavioral analytics for dynamic access control
Cryptographic Audit Ledger: Hash-linked event chains with digital signatures ensuring audit log integrity and non-repudiation
GitOps Policy Management: Immutable policy repository with signed commits, CI/CD validation, and automated drift detection
Threat Model & TTP Focus:
ROLE_DRIFT_EXPLOIT
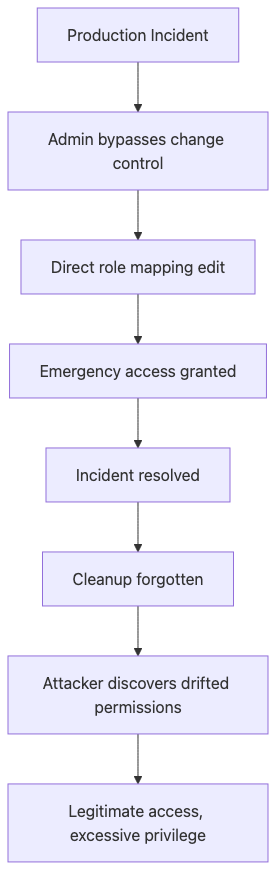
Scenario: Admin manually patches role mappings during outage, forgets to revert.
Why it works: No git history on live config changes, no approval workflow.
ATT&CK: T1098.003 (Additional Cloud Roles).
Detection: Monitor role->perm mappings in k8s configmaps, alert on drift.
Prevention: Force all RBAC changes through signed git commits with CODEOWNERS.
Real example: Contractor kept FINANCE_EXPORT perms for 3 months after project end.
This attack represents the classic "emergency access" trap that haunts enterprise environments. During production incidents, administrators bypass normal change management to quickly grant permissions, intending to review and revert changes later. However, post-incident cleanup rarely happens completely. The attack window opens when these temporary privileges become permanent through neglect. Attackers who compromise accounts with drifted roles gain access far beyond what the user should have. The insidious nature of this attack is that it appears legitimate in logs - the user has valid permissions, just more than intended.
ORPHAN_ROLE_TAKEOVER
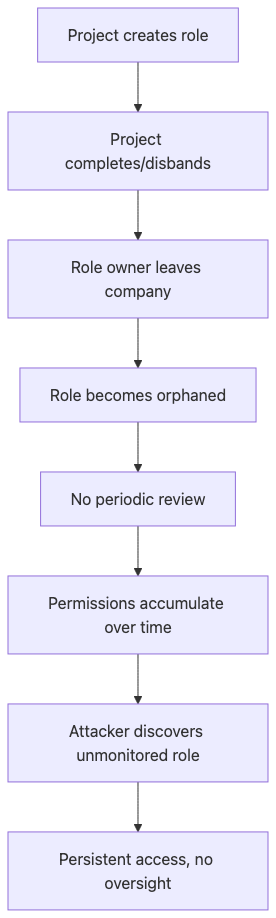
Scenario: Roles exist without business owner, nobody monitors who has them.
Why it works: No role lifecycle management, no periodic access reviews.
ATT&CK: T1078.004 (Cloud Accounts) + T1562.007 (Disable Security Tools).
Detection: Weekly scan for roles not in approved registry, alert SOC.
Prevention: Every role needs owner in LDAP, auto-expire after 90d without attestation.
Real example: LEGACY_API_READER role had 50+ users, no one knew what it did.
Orphan roles are the digital equivalent of master keys that nobody remembers creating. These roles typically originate from disbanded projects, departed employees, or organizational restructuring. Without clear ownership, they escape regular review cycles and accumulate permissions over time. Attackers target these roles because they offer persistent access with minimal oversight. The challenge is that removing an orphan role requires understanding its purpose, but the context has been lost. Organizations often keep these roles "just in case," creating permanent attack vectors.
SHADOW_ADMIN_ESCALATION
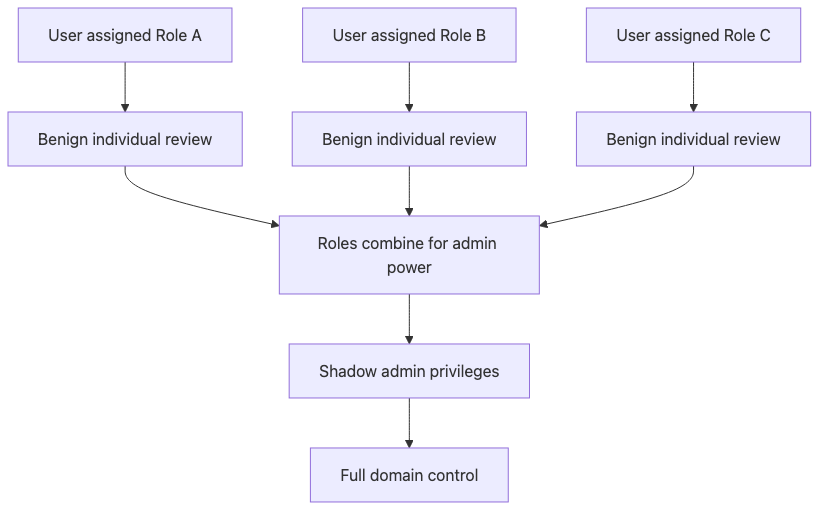
Scenario: User accumulates innocent roles that together = root access.
Why it works: No toxic combination analysis, roles reviewed individually.
ATT&CK: T1484.002 (Trust Modification) + T1069.003 (Cloud Groups).
Detection: Graph analysis for privilege aggregation paths, SoD violations.
Prevention: Real-time check if new role assignment creates admin-equivalent perms.
Real example: USER_ADMIN + BACKUP_RESTORE + LOG_VIEWER = full domain control.
This represents the most sophisticated RBAC attack vector, exploiting the complexity of modern permission systems. Individual roles appear benign when reviewed in isolation, but their intersection creates dangerous privilege combinations. For example, USER_ADMIN + BACKUP_RESTORE + LOG_VIEWER allows creating accounts, accessing all data through backups, and hiding activities in logs. Attackers patient enough to accumulate roles gradually can achieve domain admin equivalent access while flying under traditional monitoring radars. The attack is particularly effective in matrix organizations where users legitimately need multiple roles across different business functions.
FAIL_OPEN_POLICY_BYPASS
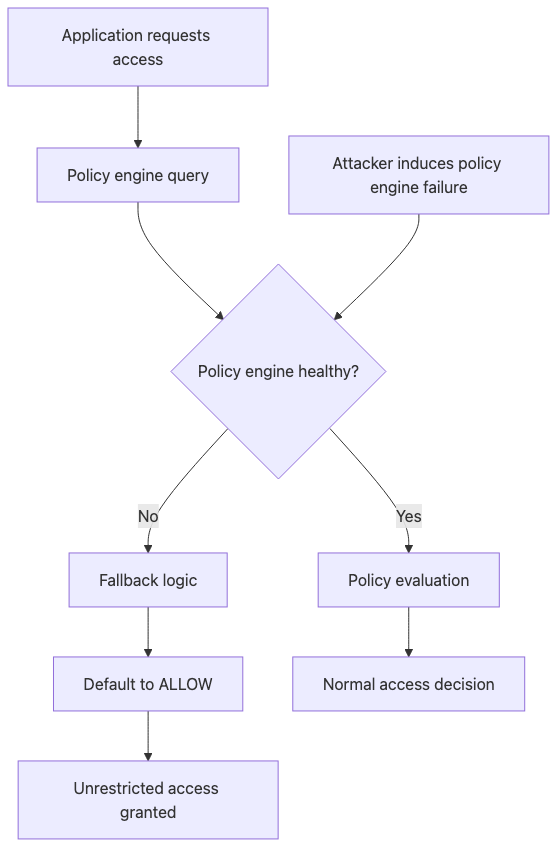
Scenario: OPA/policy engine returns 500, app defaults to ALLOW instead of DENY.
Why it works: Exception handling assumes temporary issue, grants access anyway.
ATT&CK: T1190 (Exploit Public-Facing Application) + T1203 (Exploitation for Client Execution).
Detection: Monitor policy engine latency/errors, correlate with access grants.
Prevention: Circuit breaker MUST fail CLOSED, cache last-known-good decisions only.
Real example: Redis crash caused OPA timeout, 6 hours of unrestricted API access.
The fail-open pattern represents a fundamental architectural flaw in availability-focused designs that prioritize uptime over security. When policy engines experience failures, well-intentioned developers implement fallback logic that defaults to granting access to maintain application functionality. This creates a critical attack surface where induced failures become privilege escalation vectors. Attackers can trigger policy engine overload through resource exhaustion, network partitioning, or dependency failures. The 6-hour window mentioned represents actual breach dwell time where every API call was granted due to Redis exhaustion causing OPA timeouts.
Implementation Patterns, Metrics & Testing:
Common Failure Modes: Deny rules evaluated after broad allow wildcard • Missing explicit default deny causing implicit allow on parsing errors • Audit write failures silently ignored • Role deletion leaves cached permissions alive in app memory.
SPRING_BOOT_RBAC_INTERCEPTOR
@Override public void addInterceptors(InterceptorRegistry registry) {
registry.addInterceptor(new RbacPolicyMiddleware()).order(1);
}
The critical implementation detail is placing this interceptor in WebMvcConfigurer to run before every controller. The circuit breaker MUST fail CLOSED - when OPA is down, deny everything, not allow everything. Cache decisions with ETag/TTL but invalidate on policy version bump. Dependencies: Hystrix/Resilience4j for circuit breaking.
EXPRESS_RBAC_MIDDLEWARE
const LRU = require('lru-cache');
const cache = new LRU({ max: 10000, ttl: 1000 * 60 * 5 });
// Cache key = user:role:resource:action hash
This middleware runs on EVERY route unless explicitly excluded. The cache key combines user:role:resource:action hash for granular caching. Include policy engine ETag in cache key for auto-invalidation. Async/await policy calls but timeout after 100ms, fail closed. Pro tip: Use cluster-wide Redis for cache sharing across instances.
GO_GRPC_RBAC_UNARY_INTERCEPTOR
grpc_middleware.WithUnaryServerChain(
grpc_auth.UnaryServerInterceptor(authFunc),
rbacInterceptor, // <-- your policy check here
)
This pattern intercepts ALL unary RPC calls using grpc_middleware.WithUnaryServerChain. Context propagation is crucial - pass decision ID via gRPC metadata for audit trails. Use go-cache with TTL for local decisions, sync with policy engine. Tool: grpc-ecosystem/go-grpc-middleware for boilerplate.
FASTAPI_RBAC_DEPENDENCY
@app.get("/sensitive-data")
async def get_data(authorized: bool = Depends(check_rbac_policy)):
if not authorized: raise HTTPException(401)
Dependency injection pattern provides clean separation of concerns. Use asyncio.gather() for parallel OPA call + context enrichment (geo, device). Use async Redis for decision caching, pickling user context objects. Pydantic models for type safety on policy request/response objects. Dependencies: asyncio-redis, pydantic for robust async operations.
Observability & Metrics: Expose rbac_decision_latency_ms, rbac_denies_total, rbac_policy_version_active, rbac_drift_events. Set SLO: p95 decision latency < 30ms; drift MTTR < 4h.
Testing Strategy: Unit golden tests for each role → action → expected decision • Policy Fuzz generate random role + action combos ensure no unexpected ALLOW • Chaos induce policy engine 500 – application must fail CLOSED • Snapshot hash of effective permissions vs previous release.
Edge Cases: Empty role header → treat as unauthenticated role not null • Policy timeout → deny + emit policy_timeout_total metric • Partial context (geo missing) → degrade to stricter baseline not allow.
Quick Wins vs Strategic:
WEEK_1_TACTICAL_FIXES
kubectl patch deployment opa-server -p '{"spec":{"template":{"spec":{"containers":[{"name":"opa","env":[{"name":"FAIL_CLOSED","value":"true"}]}]}}}}'
echo "audit_hash=$(echo $prev_hash:$decision | sha256sum)" >> /var/log/rbac/decisions.log
cp scripts/pre-commit-sign-rbac .git/hooks/pre-commit && chmod +x .git/hooks/pre-commit
Critical quick wins that can be implemented in under a week. The circuit breaker fail-closed toggle (30min) is the highest priority - when OPA is down, deny everything. Hash-chained audit logging (2 hours) creates tamper-evident decision trails where each decision links to the previous hash. Git commit signing hooks (4 hours) force GPG signatures on all RBAC policy changes plus CODEOWNERS file requiring 2x security team approval.
QUARTER_1_STRATEGIC_BUILDS
def detect_shadow_admin(user_roles):
combined_perms = set()
for role in user_roles:
combined_perms.update(get_permissions(role))
return is_admin_equivalent(combined_perms)
Long-term strategic initiatives requiring significant development effort. Toxic role combination analyzer (6 weeks) uses Neo4j graph of permissions to detect privilege escalation paths. Real-time RBAC anomaly ML model (8 weeks) applies unsupervised learning on access patterns with features like user_id, resource_type, time_of_day, geo_location, failure_rate using IsolationForest. Formal verification (12 weeks) provides mathematical proof that Cedar policies are consistent and complete using Z3 SMT solver to verify policy invariants.
Attack Sequence (Privilege Escalation via Silent Role Drift)
Security Diagrams
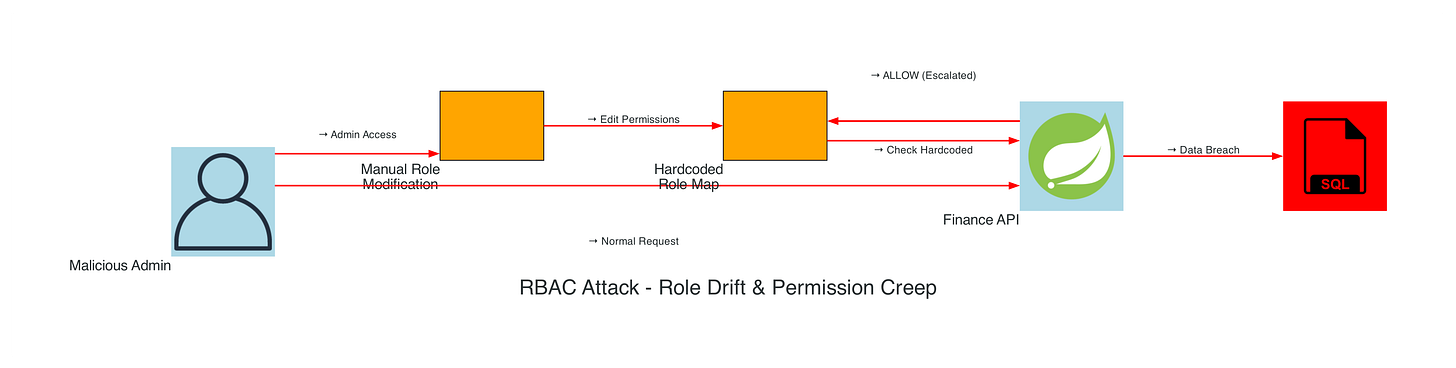
RBAC Attack - Role Drift & Permission Creep
The RBAC attack diagram illustrates the systematic exploitation of role-based access control weaknesses through permission creep and configuration drift. This visualization shows how attackers leverage manual role modifications, orphaned permissions, and shadow admin privilege aggregation to escalate access. The diagram demonstrates the attack flow from initial role manipulation through persistent access maintenance, highlighting the critical failure points where organizations lose visibility into their permission landscape. Key attack vectors include exploiting hardcoded role mappings, leveraging stale cached permissions, and taking advantage of missing change management processes that allow unauthorized role modifications to persist undetected.
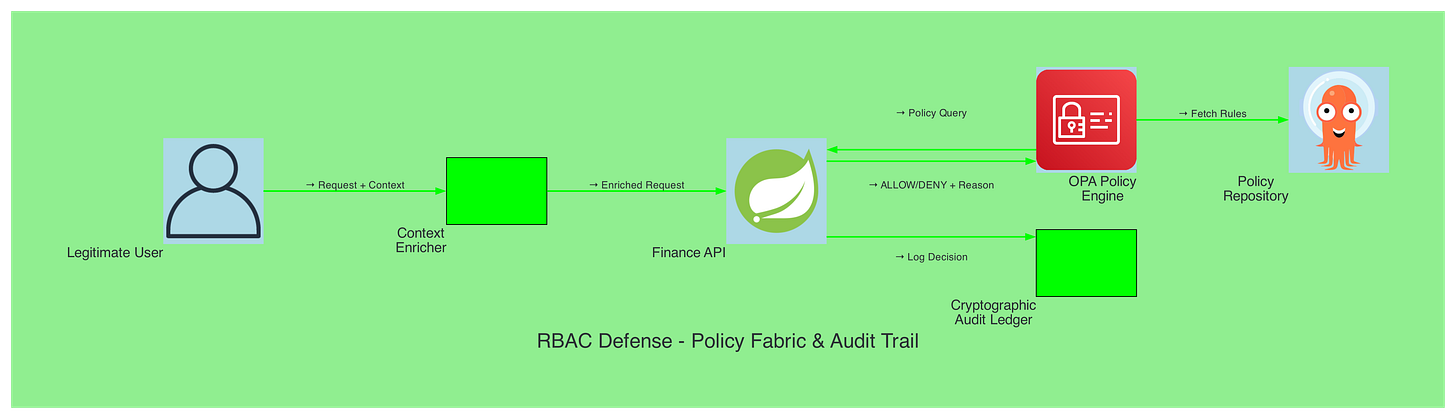
RBAC Defense - Policy Fabric & Audit Trail
The RBAC defense architecture diagram showcases a comprehensive policy-driven approach to role-based access control that eliminates common attack vectors through externalized policy engines and cryptographic audit trails. This architectural blueprint demonstrates how organizations can implement tamper-evident permission management using OPA/Cedar policy engines with signed commits and automated drift detection. The diagram emphasizes the critical security controls including hash-linked audit chains, real-time risk scoring integration, and fail-closed circuit breaker patterns that ensure robust access control even during system failures. The policy fabric approach shown here represents the gold standard for enterprise RBAC implementations that can withstand sophisticated insider threats and privilege escalation attacks.