Secure by Design Execution and File Management
From File Upload to Execution: A Comprehensive Guide to Modern File System Security
Abstract
In the complex ecosystem of modern enterprise applications, file execution and management have become the silent battlegrounds where attackers establish persistent footholds, escalate privileges, and exfiltrate sensitive data through increasingly sophisticated, multi-stage, and supply-chain driven attacks. This comprehensive guide explores the implementation of secure-by-design file management architectures, examining critical vulnerabilities in file handling pipelines and providing battle-tested, framework-agnostic solutions across cloud, on-premises, and hybrid environments. Through real-world attack scenarios and defensive strategies, we uncover why traditional perimeter-focused file security models fail and how to architect resilient, observable, self-defending file management systems that remain secure under pressure. The objective is to enable teams to shift file security left, embed continuous verification, and operationalize measurable controls rather than relying on ad-hoc patches.
Key Topics Covered:
File execution attack vectors: Malicious uploads, sandbox escapes, container breakouts
Secure file management patterns across cloud and on-premises architectures
Advanced defense mechanisms: Sandboxing, integrity monitoring, encrypted storage
Production-ready implementations with security annotations
Comprehensive detection rules and monitoring strategies for file operations
The Silent Infiltration: When File Operations Become Attack Vectors
Picture this: A financial services company processes loan documents through an automated underwriting system. The developers implement robust API security - OAuth 2.0, rate limiting, input validation. But they overlook a critical detail: the document processing service executes uploaded files in a container with elevated privileges. An attacker crafts a malicious PDF containing embedded JavaScript that breaks out of the sandbox, escalates to root privileges, and establishes persistence through a cryptocurrency mining botnet. Within days, the company's cloud infrastructure is compromised, processing power is being sold on dark markets, and regulatory compliance is shattered - all because of a seemingly innocent file upload.
This scenario illustrates the fundamental shift in modern application security. As organizations digitize document workflows, file operations transform from simple storage mechanisms into complex execution environments. Unlike traditional network-based attacks that can be blocked at firewalls, file-based attacks are invited inside - uploaded by users, processed by trusted systems, and executed in privileged contexts.
AWS_S3_PRESIGNED_URL_EXPLOITATION
AWS S3 Pre-signed URLs provide time-limited access to private objects, but weak generation practices, URL manipulation, privilege escalation, and systematic exploitation create extensive attack surfaces for unauthorized data access, bucket enumeration, and persistent compromise through signature harvesting, policy abuse, and economic exploitation of cloud storage infrastructure.
Phase 1: Initial URL Acquisition (T+0 to T+24 hours)
Email Interception: Monitor corporate communications for shared presigned URLs
Network Traffic Analysis: MITM attacks on unsecured WiFi to harvest URLs from HTTP traffic
Social Engineering: Phishing campaigns targeting employees with S3 access
Third-Party Integrations: Exploit API endpoints that generate presigned URLs for external services
Phase 2: URL Analysis and Validation (T+1 day to T+3 days)
Parameter Decomposition: Extract AWS access key ID, signature algorithm, expiration timestamp, policy conditions
Signature Validation: Verify URL cryptographic integrity and remaining time window
Permission Probing: Test URL with minimal requests to avoid detection triggers
Baseline Establishment: Identify legitimate access patterns for evasion modeling
Phase 3: Systematic Exploitation (T+3 days to T+30 days)
Exploitation Decision Tree
├── URL Expiration Analysis
│ ├── Short-Term (< 1 hour) → Immediate Mass Download
│ ├── Medium-Term (1-24 hours) → Selective High-Value Targeting
│ └── Long-Term (> 24 hours) → Comprehensive Enumeration Campaign
├── IAM Permission Assessment
│ ├── Read-Only Access → Focus on Data Exfiltration
│ ├── List Permissions → Execute Bucket Enumeration
│ ├── Write Access → Deploy Persistence Mechanisms
│ └── Admin Privileges → Launch Privilege Escalation
├── Bucket Security Configuration
│ ├── Public Read → Direct Content Access
│ ├── Private with ACLs → ACL Manipulation Attempts
│ ├── Encrypted Storage → Key Management Exploitation
│ └── VPC Endpoints → Network Lateral Movement
└── Business Context Integration
├── Financial Services → Target Transaction Logs
├── Healthcare → Focus on PHI/Medical Records
├── Technology → Intellectual Property Theft
└── Government → Classified Document Hunting
Phase 4: Advanced Persistence and Expansion (T+30 days+)
Credential Harvesting Techniques:
AWS CLI Configuration Mining: Search for
.aws/credentialsfiles in accessible directoriesEnvironment Variable Extraction: Probe application configuration for hardcoded AWS keys
Instance Metadata Exploitation: Access EC2 metadata endpoints for temporary credentials
Cross-Account Role Enumeration: Test assume-role capabilities for privilege escalation
Long-Term Access Establishment:
IAM User Creation: Create backup IAM users with programmatic access for persistent entry
S3 Bucket Policy Modification: Add attacker-controlled principals to bucket policies
Lambda Function Injection: Deploy malicious Lambda functions triggered by S3 events
CloudTrail Log Manipulation: Modify or disable logging to hide ongoing activities
Attack Scenarios:
Target Environment: Investment bank with algorithmic trading platform
Attack Objective: Trading algorithm theft for competitive advantage and market manipulation
Attack Progression:
Corporate Espionage Phase: Social engineering targeting quantitative analysts with fake job opportunities
URL Acquisition: Presigned URL captured from email containing "backtesting report links"
Algorithm Reconnaissance: Systematic download of trading models, risk parameters, historical performance data
Infrastructure Mapping: Bucket enumeration reveals production/staging environment structure
Credential Escalation: AWS access keys discovered in configuration backups enabling write permissions
Malicious Model Injection: Modified trading algorithms uploaded to staging environment for market manipulation
Data Persistence: Lambda backdoors installed for ongoing algorithm theft and market intelligence gathering
Economic Impact Analysis:
Intellectual Property Value: $50M in proprietary algorithms and trading strategies
Market Manipulation Potential: $200M in trading profits through front-running and algorithm gaming
Regulatory Consequences: $75M in SEC fines, trading license suspension, executive criminal charges
Advanced Detection Evasion Techniques:
Traffic Pattern Obfuscation:
Request Rate Limiting: Randomized delays between requests to mimic human behavior
User-Agent Rotation: Dynamic browser fingerprinting to avoid signature-based detection
Geographic Distribution: Proxy chains and VPN rotation to distribute traffic sources
Legitimate Session Blending: Interleave malicious requests with normal application traffic
Signature Analysis Evasion:
Parameter Order Manipulation: Reorder URL parameters while preserving signature validity
Encoding Variation: Use URL encoding variants (%20 vs + for spaces) to evade pattern matching
Header Injection: Custom HTTP headers to bypass signature verification in proxy environments
Protocol Downgrade: HTTP vs HTTPS switching to exploit protocol handling differences
Advanced S3 Exploitation Chain:
Java Spring Security:
@Service
public class S3ExploitService {
public void exploitPresignedUrl(String interceptedUrl) {
URI uri = URI.create(interceptedUrl);
Map<String, String> params = parseQuery(uri.getQuery());
String[] maliciousPaths = {
"../admin/secrets.txt", "../../backup/database.sql",
"../../../root/.aws/credentials", "logs/access.log"
};
Arrays.stream(maliciousPaths).forEach(path -> {
String modifiedUrl = String.format("https://%s/%s?%s",
uri.getHost(), path, uri.getQuery());
RestTemplate rest = new RestTemplate();
try {
ResponseEntity<byte[]> response = rest.getForEntity(modifiedUrl, byte[].class);
if (response.getStatusCode().is2xxSuccessful()) {
exfiltrateData(response.getBody());
}
} catch (Exception e) { /* handle */ }
});
}
}
.NET Core:
[Service]
public class S3ExploitService {
public async Task ExploitPresignedUrl(string interceptedUrl) {
var uri = new Uri(interceptedUrl);
var maliciousPaths = new[] {
"../admin/secrets.txt", "../../backup/database.sql",
"../../../root/.aws/credentials", "logs/access.log"
};
using var client = new HttpClient();
foreach (var path in maliciousPaths) {
var modifiedUrl = $"https://{uri.Host}/{path}?{uri.Query}";
var response = await client.GetAsync(modifiedUrl);
if (response.IsSuccessStatusCode) {
var content = await response.Content.ReadAsByteArrayAsync();
await ExfiltrateData(content);
}
}
}
}
AWS S3 Pre-signed URL Attack:
Threat Summary: Exploitation of weak pre-signed URL generation, signature validation, and IAM policy misconfiguration to achieve unauthorized S3 object access, bucket enumeration, and persistent data exfiltration beyond intended access windows.
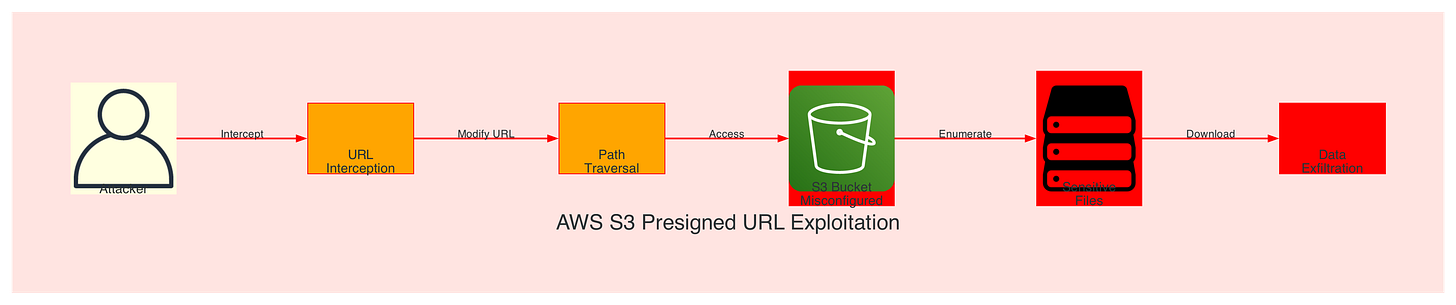
AWS S3 Exploitation Attack Flow:
Figure 5: S3 pre-signed URL exploitation attack showing path traversal and unauthorized bucket enumeration
S3 Security Hardening Defense:
Figure 6: Comprehensive S3 security controls including strict bucket policies, KMS encryption, access logging, and CloudTrail auditing
Real-World Case Study: Capital One Breach (2019) - Exploited misconfigured S3 bucket permissions and overpermissive IAM roles to access pre-signed URLs for sensitive customer data, affecting 100 million customers.
XSS_TO_LFI_PDF_PROCESSING_CHAIN
Cross-Site Scripting (XSS) in PDF processing applications creates sophisticated attack chains when combined with Local File Inclusion (LFI) vulnerabilities, template injection flaws, and server-side processing weaknesses to achieve remote code execution, comprehensive file system access, and enterprise data exfiltration through weaponized PDF documents containing multi-stage JavaScript payloads.
Environmental Prerequisites for Successful Exploitation: